Many readers are asking what they should be doing in response to Yahoo‘s disclosure Wednesday that a billion of its user accounts were hacked. Here are a few suggestions and pointers, fashioned into a good old Q&A format.

Image: eff.org
Q: Was my account hacked?
A: Experts I’ve spoken to believe Yahoo has about a billion active accounts. So, yes, it’s very likely your account’s password is compromised, and probably most of the other information you at one point entrusted to Yahoo. According to a statement from the company, the stolen user account information may have included names, email addresses, telephone numbers, dates of birth, hashed passwords (using MD5) and, in some cases, encrypted or unencrypted security questions and answers.”
Q: I’m not sure if I have a Yahoo account. How do I find out?
A: This is a surprisingly complex question. Thanks to the myriad mergers and business relationships that Yahoo has forged over the years, you may have a Yahoo account and not realize it. That’s because many accounts that are managed through Yahoo don’t actually end in “yahoo.com” (or yahoo. insert country code here).
For example, British telecom giant BT uses Yahoo for their customer email, as did/do SBCGlobal, AT&T and BellSouth. Also, Verizon.net email addresses were serviced by Yahoo until AOL took over. Up in Canada, Rogers.net customers may also have Yahoo email addresses. I’m sure there are plenty of others I’m missing, but you get the point: Your Yahoo account may not include the word “yahoo” at all in the address.
Q: I created a Yahoo account a few years ago, but Yahoo says it doesn’t exist anymore. What’s going on here?
A: Yahoo occasionally deactivates or deletes accounts that remain dormant for more than a year. If you haven’t touched your account in years, that’s probably why.
Q: Why would someone want to hack my email account? What could they do with it?
A: Spam, spam, and spam. Oh, and spam. They want to spam your contacts with malware and ads for dodgy products and services. Also, it gives the bad guys direct access to any account that you have signed up for using that email address. Why? Because if the crooks have access to your inbox, they can request a password reset link be sent to your inbox from any Web site you’ve signed up with at that email address.
For more detail on why these lowlifes might want control over your inbox and how they can monetize that access, see one of the most-read pieces on this blog — The Value of a Hacked Email Account. NB: Accounts that are hijacked for use in spam campaigns may also be suspended or deleted by Yahoo.
Q: What the heck is an MD5?
A: It’s an inferior password storage method that too many companies still use to protect user passwords. And MD5 “hash” is computed by taking your plain text password and running it against an algorithm that is supposed to make the output impossible to reverse. For example, the world’s worst password — “password” — always computes to the MD5 hash of “cc3a0280e4fc1415930899896574e118” (see this MD5 generator for more examples).
The problem is that computing power is super cheap nowadays, and MD5s are no match for brute-force attacks that simply compare the result of hashed dictionary words and other common passwords with user password databases stored in MD5 format (i.e., if the MD5 your email provider stores for you is “cc3a0280e4fc1415930899896574e118”, then congrats on using the world’s worst password).
Long story short, there are vast indexes of these pre-computed MD5 hashes — known as “rainbow tables” — freely available online that can be used to quickly crack a large percentage of any MD5 password list.
Q: So if using hashing methods like MD5 is such a lame security idea, why is Yahoo still doing this?
A: Yahoo says this breach dates back to 2013. To its credit, Yahoo began moving away from using MD5s for new accounts in 2013 in favor of Bcrypt, far more secure password hashing mechanism. But yeah, even by 2013 anyone with half a clue in securing passwords already long ago knew that storing passwords in MD5 format was no longer acceptable and altogether braindead idea. It’s one of many reasons I’ve encouraged my friends and family to ditch Yahoo email for years.
Q: I’ve been using Yahoo for years. If this service can’t be trusted, what would you recommend?
A: I’ve used Google Mail (Gmail) for more than a decade, but your mileage may vary. I moved virtually all of my email activity to Gmail years ago mainly because they were among the first to offer more robust authentication and security measures, such as two-step authentication. And they continue to innovate in this space. If you’d like to migrate the messages from your Yahoo account to a Gmail account, see these instructions.
Q: Yahoo said in some cases encrypted or unencrypted security questions and answers were stolen. Why is this a big deal?
A: Because for years security questions have served as convenient backdoors used by criminals to defraud regular, nice people who answer questions honestly. With the proliferation of data that many people post online about themselves on social media sites — combined with the volume of public records that are indexed by various paid and free services — it’s never been easier for a strange to answer your secret question, “What was the name of your elementary school?”
Don’t feel bad if you naively answered your secret questions honestly. Even criminals get their accounts hacked via easily-guessed secret questions, as evidenced by this story about the San Francisco transit extortionist who last month had his own account hacked via weak secret questions.
Q: So should I change my secret questions in my Yahoo account? Yahoo says it has “invalidated unencrypted security questions and answers so that they cannot be used to access an account,” but how do I know whether my security questions were encrypted or not?
A: Assuming you still can, yes by all means change the answers to the security questions to something only you know. However, it’s not clear that this is still an option: I tried logging in using the secret questions on two older accounts I have and did not see that option available anymore, so it’s likely that Yahoo has disabled them altogether. Yahoo’s statement on this matter is confusing, and the company hasn’t responded yet to follow-up questions to clarify the matter.
More importantly, if you have used these questions and answers at other sites, please change those answers at the other sites now. Pro tip: If you must patronize sites that allow password and account recovery via secret questions, don’t answer the secret questions honestly. Pick answers that aren’t obvious and that can’t be found using social media or a search engine.
Q: Yahoo also said that the intruders were able to forge “cookies.” What’s that all about?
A: Yahoo said the attackers had worked out a way to forge cookies, text files that Yahoo places on user computers when they log in. Authentication cookies contain information about the user’s session with Yahoo, and these cookies can contain a great deal of information about the user, such as whether that the user has already authenticated to the company’s servers.
The attackers in this case apparently found a way to forge these authentication cookies, which would have granted them to access targeted accounts without needing to supply the account’s password. In addition, a forged cookie could have allowed the attackers to remain logged into the hacked accounts for weeks or indefinitely.
Yahoo’s statement said the company is in the process of notifying the affected account holders, and that it has invalidated the forged cookies.
Q: That sounds pretty bad.
A: Yeah, that’s about as bad as it gets. It’s yet another reason I’m tell people to run away from Yahoo email.
Q: Okay, I don’t need my account anymore, and/or I’ve transferred what I need from that account and no longer want to have an account at Yahoo. Can I delete my account?
A: Yes, you can delete your account. Yahoo has detailed instructions here. But before you do this, consider whether you have created unique relationships with any other Web sites using this email account. If so, you may lose access to those third-party Web site accounts if you no longer have access to the email inbox you used to create that relationship. Take stock of any third-party Web site user accounts you may have tied to your Yahoo inbox, and if you wish to keep those accounts you’ll probably need to log in to them separately and change the contact email address.
Q: What else should I be concerned about as a result of this latest hack?
A: Make sure you have not used your Yahoo password at any other sites or online accounts that you value or that hold potentially sensitive information about you. If you have, change the password at those other sites to unique, complex passwords. And stop re-using passwords: It’s probably the leading cause of account compromises.
Also, be on the lookout for an uptick in possibly much more targeted email phishing and malware attacks. When attackers have a lot of details about you (like the ones Yahoo said were stolen in this hack) it makes it much easier for them to craft convincing email lures. Be especially wary of clicking on links or attachments in emails you were not expecting, and never respond to login or password reset requests sent via email that you did not initiate.
If your mobile phone number was associated with your Yahoo account, that number may receive SMS phishing or “smishing” attacks as a result. The standard warning about clicking links applies to unbidden text messages as well.
Enable any and all security measures available to you at your current or new email provider. The most important steps you can take are adding a backup email account that you can use to receive messages or password resets if you somehow lose access to your account (i.e., someone figures out your password and seizes control over your account), and taking advantage of two-step or two-factor authentication. With this new feature enabled, thieves would have to know your username, password, and have access to your mobile device or impersonate you to your mobile provider in order to hijack your account. For more on which providers offer this vital security feature, see twofactorauth.org. If you’re sticking with Yahoo despite all of the above, please make sure to take advantage of their two-step feature, called Yahoo Account Key.
from
https://krebsonsecurity.com/2016/12/my-yahoo-account-was-hacked-now-what/


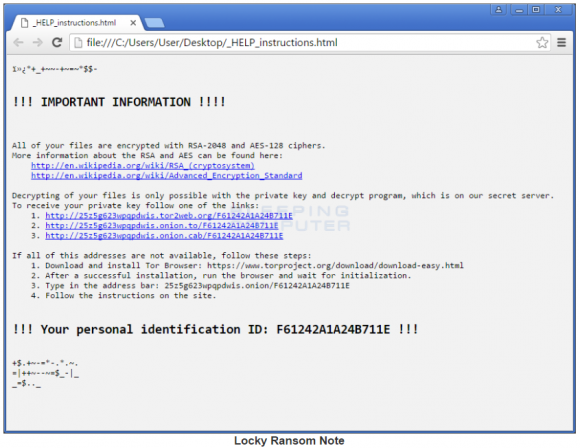
 Villain: You MUST pay the ransom!
Villain: You MUST pay the ransom!




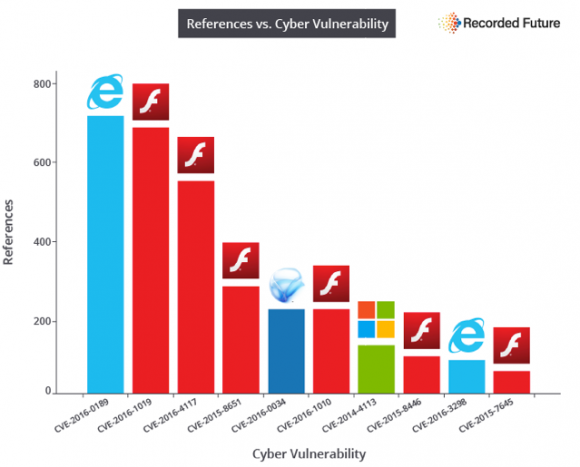

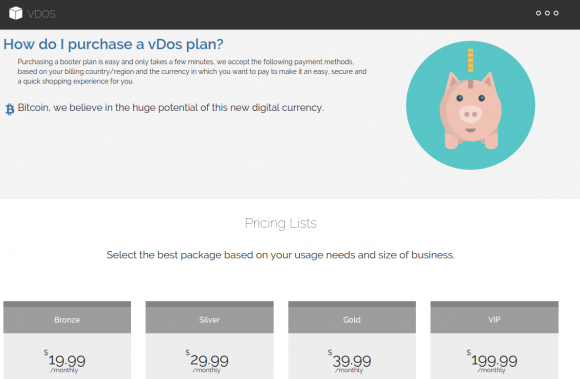






 “The private sector and the Administration should collaborate on a roadmap for improving the security of digital networks, in particular by achieving robustness against denial-of-service, spoofing, and other attacks on users and the nation’s network infrastructure,” reads the first and foremost cybersecurity recommendation for President-elect Donald Trump. “The urgency of the situation demands that the next Administration move forward promptly on our recommendations, working closely with Congress and the private sector.”
“The private sector and the Administration should collaborate on a roadmap for improving the security of digital networks, in particular by achieving robustness against denial-of-service, spoofing, and other attacks on users and the nation’s network infrastructure,” reads the first and foremost cybersecurity recommendation for President-elect Donald Trump. “The urgency of the situation demands that the next Administration move forward promptly on our recommendations, working closely with Congress and the private sector.”