Richard Smith — who resigned as chief executive of big-three credit bureau Equifax this week in the wake of a data breach that exposed 143 million Social Security numbers — is slated to testify in front of no fewer than four committees on Capitol Hill next week. If I were a lawmaker, here are some of the questions I’d ask when Mr. Smith goes to Washington.

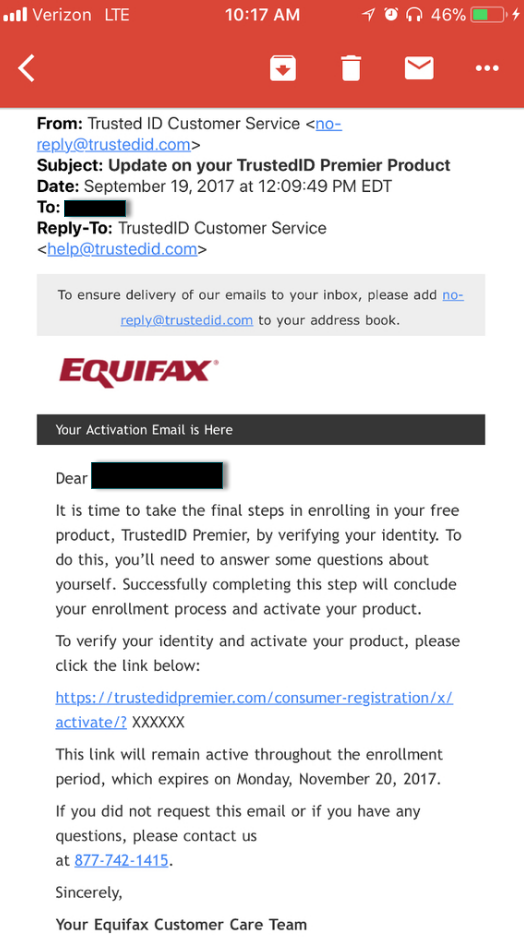
Before we delve into the questions, a bit of background is probably in order. The new interim CEO of Equifax — Paulino do Rego Barros Jr. — took to The Wall Street Journal and other media outlets this week to publish a mea culpa on all the ways Equifax failed in responding to this breach (the title of the op-ed in The Journal was literally “I’m sorry”).
“We were hacked,” Barros wrote. “That’s the simple fact. But we compounded the problem with insufficient support for consumers. Our website did not function as it should have, and our call center couldn’t manage the volume of calls we received. Answers to key consumer questions were too often delayed, incomplete or both.”
Barros stated that Equifax was working to roll out a new system by Jan. 31, 2018 that would let consumers “easily lock and unlock access to their Equifax credit files.”
“You will be able to do this at will,” he continued. “It will be reliable, safe, and simple. Most significantly, the service will be offered free, for life.”
I have argued for years that all of the data points needed for identity thieves to open new lines of credit in your name and otherwise ruin your credit score are available for sale in the cybercrime underground. To be certain, the Equifax breach holds the prospect that ID thieves could update all that stolen data with newer records. I’ve argued that the only sane response to this sorry state of affairs is for consumers to freeze their files at the bureaus, which blocks potential creditors — and ID thieves — from trashing your credit file and credit score.
Equifax is not the only bureau promoting one of these lock services. Since Equifax announced its breach on Sept. 7, big-three credit bureaus Trans Union and Experian have worked feverishly to steer consumers seeking freezes toward these locks instead, arguing that they are easier to use and allow consumers to lock and unlock their credit files with little more than the press of a button on a mobile phone app. Oh, and the locks are free, whereas the bureaus can (and do) charge consumers for placing and/or thawing a freeze (the laws freeze fee laws differ from state to state).
CREDIT FREEZE VS. CREDIT LOCK
My first group of questions would center around security freezes or credit freezes, and the difference between those and these credit lock services being pushed hard by the bureaus.
Currently, even consumer watchdog groups say they are uncertain about the difference between a freeze and a lock. See this press release from Thursday by U.S. PIRG, the federation of state Public Interest Research Groups, for one such example.
Also, I’m curious to know what percentage of Americans had a freeze prior to the breach, and how many froze their credit files (or attempted to do so) after Equifax announced the breach. The answers to these questions may help explain why the bureaus are now massively pushing their new credit lock offerings (i.e., perhaps they’re worried about the revenue hit they’ll take should a significant percentage of Americans decide to freeze their credit files).
I suspect the pre-breach number is less than one percent. I base this guess loosely on some data I received from the head of security at Dropbox, who told KrebsOnSecurity last year that less than one percent of its user base of 500 million registered users had chosen to turn on 2-factor authentication for their accounts. This extra security step can block thieves from accessing your account even if they steal your password, but many consumers simply don’t take advantage of such offerings because either they don’t know about them or they find them inconvenient.
Bear in mind that while most two-factor offerings are free, most freezes involve fees, so I’d expect the number of pre-breach freezers to be a fraction of one percent. However, if only one half of one percent of Americans chose to freeze their credit files before Equifax announced its breach — and if the total number of Americans requesting a freeze post-breach rose to, say, one percent — that would still be a huge jump (and potentially a painful financial hit to Equifax and the other bureaus).

So without further ado, here are some questions I’d ask on the topic of credit locks and freezes:
-Approximately how many credit files on Americans does Equifax currently maintain?
-Prior to the Equifax breach, approximately how many Americans had chosen to freeze their credit files at Equifax?
-Approximately how many total Americans today have requested a freeze from Equifax? This should include the company’s best estimate on the number of people who have requested a freeze but — because of the many failings of Equifax’s public response cited by Barros — were unable to do so via phone or the Internet.
-Approximately how much does Equifax charge each time the company sells a credit check (i.e., a bank or other potential creditor performs a “pull” on a consumer credit file)?
-On average, how many times per year does Equifax sell access to consumer’s credit file to a potential creditor?
-Mr. Barros said Equifax will extend its offer of free credit freezes until the end of January 2018. Why not make them free indefinitely, just as the company says it plans to do with its credit lock service?
-In what way does a consumer placing a freeze on their credit file limit Equifax’s ability to do business?
-In what way does a consumer placing a lock on their credit file limit Equifax’s ability to do business?
-If a lock accomplishes the same as a freeze, why create more terminology that only confuses consumers?
-By agreeing to use Equifax’s lock service, will consumers also be opting in to any additional marketing arrangements, either via Equifax or any of its partners?
BREACH RESPONSE
Equifax could hardly have bungled their breach response more if they tried. It is said that one should never attribute to malice what can more easily be explained by incompetence, but Equifax surely should have known that how they handled their public response would be paramount to their ability to quickly put this incident behind them and get back to business as usual.

Equifax has come under heavy criticism for waiting too long to disclose this breach. It has said that the company became aware of the intrusion on July 29, and yet it did not publicly disclose the breach until Sept. 7.However, when Equifax did disclose, it seemed like everything about the response was rushed and ill-conceived.
One theory that I simply cannot get out of my head is that perhaps Equifax rushed preparations for is breach disclosure and response because it was given a deadline by extortionists who were threatening to disclose the breach on their own if the company did not comply with some kind of demand.
-I’d ask a question of mine that Equifax refused to answer shortly after the breach: Whether the company was the target of extortionists over this data breach *before* the breach was officially announced on Sept. 7.
-Equifax said the attackers abused a vulnerability in Apache Struts to break in to the company’s Web applications. That Struts flaw was patched by the Apache Foundation on March 8, 2017, but Equifax waited until after July 30, 2017 — after it learned of the breach — to patch the vulnerability. Why did Equifax decide to wait four and a half months to apply this critical update?
-How did Equifax become aware of this breach? Was it from an external source, such as law enforcement?
-Assuming Equifax learned about this breach from law enforcement agencies, what did those agencies say regarding how they learned about the breach?
FRAUD AND ABUSE
Multiple news organizations have reported that companies which track crimes related to identity theft — such as account takeovers, new account fraud, and e-commerce fraud — saw huge upticks in all of these areas corresponding to two periods that are central to Equifax’s breach timeline; the first in mid-May, when Equifax said the intruders began abusing their access to the company, and the second late July/early August, when Equifax said it learned about the breach.
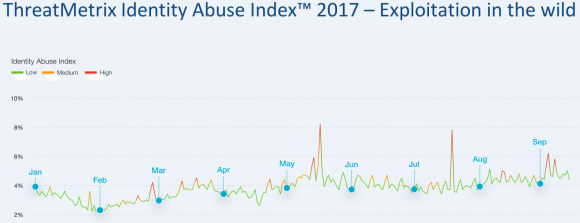
This chart shows spikes in various forms of identity abuse — including account takeovers and new account fraud — as tracked by ThreatMetrix, a San Jose, Calif. firm that helps businesses prevent fraud.
-Has Equifax performed any analysis on consumer credit reports to determine if there has been any pattern of consumer harm as a result of this breach?
-Assuming the answer to the previous question is yes, did the company see any spikes in applications for new lines of consumer credit corresponding to these two time periods in 2017?
Many fraud experts report that a fast-growing area of identity theft involves so-called “synthetic ID theft,” in which fraudsters take data points from multiple established consumer identities and merge them together to form a new identity. This type of fraud often takes years to result in negative consequences for consumers, and very often the debt collection agencies will go after whoever legitimately owns the Social Security number used by that identity, regardless of who owns the other data points.
-Is Equifax aware of a noticeable increase in synthetic identity theft in recent months or years?
-What steps, if any, does Equifax take to ensure that multiple credit files are not using the same Social Security number?
-Prior to its breach disclosure, Equifax spent more than a half million dollars in the first half of 2017 lobbying Congress to pass legislation that would limit the legal liability of credit bureaus in connection with data security lapses. Do you still believe such legislation is necessary? Why or why not?
What questions did I leave out, Dear Readers? Or is there a way to make a question above more succinct? Sound off in the comments below, and I may just add yours to the list!
In the meantime, here are the committees at which Former Equifax CEO Richard Smith will be testifying next week on Capitol Hill. Some of these committees will no doubt be live-streaming the hearings. Check back at the links below on the morning-of for more information on that. Also, C-SPAN almost certainly will be streaming some of these as well:
-Tuesday, Oct. 3, 10:00 a.m., House Energy and Commerce Committee. Rayburn House Office Bldg. Room 2123.
-Wednesday, Oct. 5, 10:00 a.m., Senate Committee on Banking, Housing, & Urban Affairs. Dirksen Senate Office Bldg., Room 538.
-Wednesday, Oct. 5, 2:30 p.m., Senate Judiciary Subcommittee on Privacy, Technology and the Law. Dirksen Senate Office Bldg., Room 226.
-Thursday, Oct. 6, 9:15 a.m., House Financial Services Committee. Rayburn House Office Bldg., Room 2128.
from
https://krebsonsecurity.com/2017/09/heres-what-to-ask-the-former-equifax-ceo/


 In
In 


 Adobe’s newest Flash version — v. 27.0.0.130 for Windows, Mac and Linx systems — corrects
Adobe’s newest Flash version — v. 27.0.0.130 for Windows, Mac and Linx systems — corrects