How much would a cybercriminal, nation state or organized crime group pay for blueprints on how to exploit a serious, currently undocumented, unpatched vulnerability in all versions of Microsoft Windows? That price probably depends on the power of the exploit and what the market will bear at the time, but here’s a look at one convincing recent exploit sales thread from the cybercrime underworld where the current asking price for a Windows-wide bug that allegedly defeats all of Microsoft’s current security defenses is USD $90,000.
So-called “zero-day” vulnerabilities are flaws in software and hardware that even the makers of the product in question do not know about. Zero-days can be used by attackers to remotely and completely compromise a target — such as with a zero-day vulnerability in a browser plugin component like Adobe Flash or Oracle’s Java. These flaws are coveted, prized, and in some cases stockpiled by cybercriminals and nation states alike because they enable very stealthy and targeted attacks.
The $90,000 Windows bug that went on sale at the semi-exclusive Russian language cybercrime forum exploit[dot]in earlier this month is in a slightly less serious class of software vulnerability called a “local privilege escalation” (LPE) bug. This type of flaw is always going to be used in tandem with another vulnerability to successfully deliver and run the attacker’s malicious code.
LPE bugs can help amplify the impact of other exploits. One core tenet of security is limiting the rights or privileges of certain programs so that they run with the rights of a normal user — and not under the all-powerful administrator or “system” user accounts that can delete, modify or read any file on the computer. That way, if a security hole is found in one of these programs, that hole can’t be exploited to worm into files and folders that belong only to the administrator of the system.
This is where a privilege escalation bug can come in handy. An attacker may already have a reliable exploit that works remotely — but the trouble is his exploit only succeeds if the current user is running Windows as an administrator. No problem: Chain that remote exploit with a local privilege escalation bug that can bump up the target’s account privileges to that of an admin, and your remote exploit can work its magic without hindrance.
The seller of this supposed zero-day — someone using the nickname “BuggiCorp” — claims his exploit works on every version of Windows from Windows 2000 on up to Microsoft’s flagship Windows 10 operating system. To support his claims, the seller includes two videos of the exploit in action on what appears to be a system that was patched all the way up through this month’s (May 2016) batch of patches from Microsoft (it’s probably no accident that the video was created on May 10, the same day as Patch Tuesday this month).
A second video (above) appears to show the exploit working even though the test machine in the video is running Microsoft’s Enhanced Mitigation Experience Toolkit (EMET), a free software framework designed to help block or blunt exploits against known and unknown Windows vulnerabilities and flaws in third-party applications that run on top of Windows.
![The sales thread on exploit[dot]in.](https://lh3.googleusercontent.com/blogger_img_proxy/AEn0k_tvLoiIV0S2wlgB4bY8RPBo6LbrVJthLJ9Aq0HBkdd_mhMyvYuTAKTPPqw9x6ZZAJRADbTprHrbOBG47_pBmFbimiSv8W6ZDwGKafJ4QTIIzs1oMXn_XYtK43EyOSzMk5ZWZhMQ27vzDWVDE5Ylag=s0-d)
The sales thread on exploit[dot]in.
Jeff Jones, a cybersecurity strategist with Microsoft, said the company was aware of the exploit sales thread, but stressed that the claims were still unverified. Asked whether Microsoft would ever consider paying for information about the zero-day vulnerability, Jones pointed to the company’s bug bounty program that rewards security researchers for reporting vulnerabilities. According to Microsoft, the program to date has paid out more than $500,000 in bounties.
Microsoft heavily restricts the types of vulnerabilities that qualify for bounty rewards, but a bug like the one on sale for $90,000 would in fact qualify for a substantial bounty reward. Last summer, Microsoft raised its reward for information about a vulnerability that can fully bypass EMET from $50,000 to $100,000. Incidentally, Microsoft said any researcher with a vulnerability or who has questions can reach out to the Microsoft Security Response Center to learn more about the program and process.
ANALYSIS
It’s interesting that this exploit’s seller could potentially make more money by peddling his find to Microsoft than to the cybercriminal community. Of course, the videos and the whole thing could be a sham, but that’s probably unlikely in this case. For one thing, a scammer seeking to scam other thieves would not insist on using the cybercrime forum’s escrow service to consummate the transaction, as this vendor has.
As I noted in my book Spam Nation, cybercrime forums run on reputation-based systems similar to eBay’s “feedback” mechanism — in the form of reputation points granted or revoked by established members. Rookie and established members alike are all encouraged to use the forum’s “escrow” system to ensure transactions are completed honorably among thieves.
The escrow service can act as a sort of proxy for reputation. The forum administrators hold the buyer’s money in escrow until the seller can demonstrate he has held up his end of the bargain, be it delivering the promised goods, services or crypto-currency. The forum admins keep a small percentage of the overall transaction amount (usually in Bitcoins) for acting as the broker and insurer of the transaction.
Thus, if a member states up front that he’ll only work through a crime forum’s escrow service, that member’s cybercriminal pitches are far more likely to be taken seriously by others on the forum.
Security researchers at Trustwave first pointed my attention to the exploit[dot]in zero-day sales thread last week. Ziv Mador, vice president of security research at Trustwave, said he believes the exploit is legitimate.
“It seems the seller has put in the effort to present himself/herself as a trustworthy seller with a valid offering,” he said. Mador noted Trustwave can’t be 100% certain of the details without the vulnerability in their possession, but that the videos and translation provide further evidence. The company has published more detail on the sales thread and the claimed capabilities of the exploit.
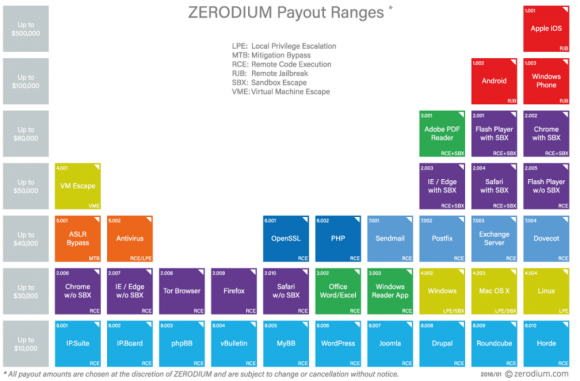
Is $90,000 the right price for this vulnerability? Depends on whom you ask. For starters, not everyone values the same types of exploits similarly. For example, the vulnerability prices listed by exploit broker Zerodium indicate that the company places a far lesser value on exploits in the Windows operating system and far more on vulnerabilities in mobile systems and Web browser components. Zerodium says the price it might be willing to pay for a similar Windows exploit is about $30,000, whereas a critical bug in Apple’s iOS mobile operating system could fetch up to $100,000.

Image: Zerodium.com
Vlad Tsyrklevich, a researcher who’s published quite a bit about the shadowy market for zero-day exploits, says price comparisons for different exploits should be taken with a grain of salt. In his analysis, Tsyrklevich points to a product catalog from exploit vendor Netragard, which in 2014 priced a non-exclusive Windows LPE vulnerability at $90,000.
“Exploit developers have an incentive to state high prices and brokers offer to sell both low-quality and high-quality exploits,” Tsyrklevich wrote. “If a buyer negotiates poorly or chooses a shoddy exploit, the vendor still benefits. Moreover, it’s difficult to compare the reliability and projected longevity of vulnerabilities or exploits offered by different developers. Many of the exploits offered by exploit brokers are not sold.”
BuggiCorp, the seller of the Windows LPE zero-day flaw, was asked by several forum members whether his zero-day was related to a vulnerability that Microsoft patched on April 12, 2016. BuggiCorp responds that his is different. But as documented by security vendor FireEye, that flaw was a similar LPE vulnerability that FireEye said was featured in a series of spear phishing attacks aimed at gaining access to point-of-sale systems at targeted retail, restaurant and hospitality industries. FireEye called the downloader used in those attacks “Punchbuggy,” but it did not specify why it chose that name.
If nothing else, this zero-day thread is an unusual sight on such an open cybercrime forum, Trustwave’s Mador said.
“Finding a zero day listed in between these fairly common offerings is definitely an anomaly,” he said. “It goes to show that zero days are coming out of the shadows and are fast becoming a commodity for the masses, a worrying trend indeed.”
from
http://redirect.viglink.com?u=http%3A%2F%2Fkrebsonsecurity.com%2F2016%2F05%2Fgot-90000-a-windows-0-day-could-be-yours%2F&key=ddaed8f51db7bb1330a6f6de768a69b8
![The sales thread on exploit[dot]in.](http://krebsonsecurity.com/wp-content/uploads/2016/05/buggicorp-580x255.png)