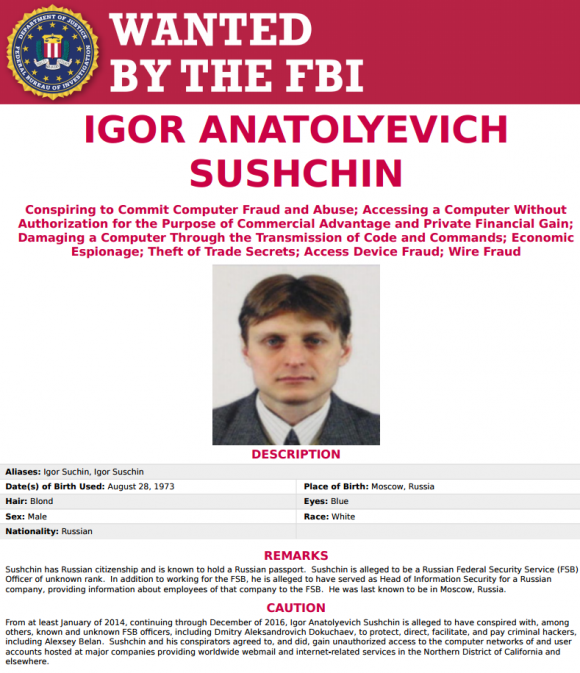
Once you understand how easy and common it is for thieves to attach “skimming” devices to ATMs and other machines that accept debit and credit cards, it’s difficult not to closely inspect and even tug on the machines before using them. Several readers who are in the habit of doing just that recently shared images of skimmers they discovered after gently pulling on various parts of a cash machine they were about to use.
Viewed from less than two feet away, this ATM looks reasonably safe to use, right?

Although it may be difficult to tell from even this close, this ATM’s card acceptance slot and cash dispenser are both compromised by skimming devices.
But something fishy comes into view when we change our perspective slightly. Can you spot what doesn’t belong here?
Can you spot what doesn’t belong here?
Congratulations if you noticed the tiny pinhole in the upper right corner of the phony black bezel that was affixed over top of the cash dispenser slot. That fake bezel overlay contained a tiny pinhole camera angled toward the PIN pad to record time-stamped videos of people entering their PINs:

A closeup of the tiny pinhole that allows a mini spy camera embedded in the fake cash dispenser bezel to record customers entering their PINs.
How about the card acceptance slot? Looks legit (if a tad shinier than the rest of the ATM), right?
What happens if we apply a tiny bit of pressure to the anti-skimming green bezel where customers are expected to insert their ATM cards? Look at that! The cheap plastic bezel that skimmer thieves placed on top of the real card acceptance slot starts to pull away. Also, you can see some homemade electronics that are not very well hidden at the mouth of the bezel.

Notice the left side of this card skimmer overlay starts to pull away from the rest of the facade when squeezed. Also note the presence of a circuit board close to the mouth of the fake bezel.
ATM card skimmers contain tiny bits of electronics that record payment card data from the magnetic stripe on the backs of cards inserted into a hacked ATM. Most commonly (as in this case), a card skimmer is paired with a pinhole spy camera hidden above or beside the PIN pad to record time-stamped video of cardholders entering their PINs. Taken together, the stolen data allows thieves to fabricate new cards and use PINs to withdraw cash from victim accounts.
Card skimmers designed to look like the green anti-skimming devices found on many ATMs are some of the most common cash machine skimming devices in use today, probably because they are relatively cheap to manufacture en masse and there are many fraudsters peddling these in the cybercrime underground.
Typically, the fake anti-skimmer bezels like the one pictured above are made of hard plastic. However, the reader who shared these images said this bezel card skimming device was made of a semi-flexible, vinyl-like plastic material.
“I immediately went in and notified the manager who shut down the machine,” the reader said in an email to KrebsOnSecurity. “All the tellers were busy so he asked me to stand by the ATM and stop people from trying to use it while he called his security team. In the three minutes I was standing there a young woman came up and started to dip her card in the slot even thought the screen was black. I stopped her and told her and pointed out what was going. She was thankful.”
Normally, these bezel skimmers look more like the hard plastic one that came off of this ATM at a 7-Eleven convenience store in Texas in February, after a customer yanked on the ATM’s card acceptance slot:
A skimmer overlay that came off an ATM at a 7-Eleven convenience store in Texas after a curious customer tugged on the card slot.
Many people believe that skimmers are mainly a problem in the United States, where most ATMs still do not require more secure chip-based cards that are far more expensive and difficult for thieves to clone. However, it’s precisely because most U.S. ATMs lack this security requirement that skimming remains so prevalent in Europe.
Mainly for reasons of backward compatibility to accommodate American tourists, many European ATMs allow non-chip-based cards to be inserted into the cash machine. What’s more, many chip-based cards issued by American and European banks alike still have cardholder data encoded on a magnetic stripe in addition to the chip.
When thieves skim ATMs in Europe, they generally sell the stolen card and PIN data to fraudsters on the other side of the pond. Those fraudsters in turn will encode the card data onto counterfeit cards and withdraw cash at ATMs here in the United States.
Interestingly, even after most U.S. banks put in place chip-capable ATMs, the magnetic stripe will still be needed because it’s an integral part of the way ATMs work: Most ATMs in use today require a magnetic stripe for the card to be accepted into the machine. The main reason for this is to ensure that customers are putting the card into the slot correctly, as embossed letters and numbers running across odd spots in the card reader can take their toll on the machines over time.
Below is part of a skimming device that a reader recently pulled off of a compromised ATM in Dusseldorf, Germany. This component actually cracked off of the hard plastic fake anti-skimming bezel that was placed by a fraudster over top of the card acceptance device of an NCR cash machine there.
Here’s the plastic overlay that the piece pictured in the reader’s hand above broke away from:
It’s fine to tug on parts of an ATM before using it (heck, I’ve been known to do this even for machines I have no intention of using), but just know that doing so doesn’t guarantee that you will detect a cleverly hidden skimmer.
As I’ve noted in countless skimmer stories here, the simplest way to protect yourself from ATM skimming is to cover your hand when entering your PIN. That’s because most skimmers rely on hidden cameras to steal the victim’s PIN. As easy as this is, you’d be amazed at how many people fail to take this basic precaution.
Yes, there is still a chance that thieves could use a PIN-pad overlay device to capture your PIN, but in my experience these are far less common than hidden cameras (and quite a bit more costly for thieves who aren’t making their own skimmers).
Also, if you visit an ATM that looks strange, tampered with, or out of place, try to find another cash machine. Use only machines in public, well-lit areas, and avoid ATMs in secluded spots. Finally, don’t neglect your own physical security while at the cash machine: As common as these skimmers are, you’re probably more likely to get mugged withdrawing cash from an ATM than you are to find a skimmer attached to it.
Did you enjoy this post? Are you fascinated by skimming devices? Check out my series, All About Skimmers.
from
https://krebsonsecurity.com/2017/03/why-i-always-tug-on-the-atm/




 In early 2007, PayPal (then part of the same company as eBay) began offering its hardware token for a one-time $5 fee, and at the time the company was among very few that were pushing this second-factor (something you have) in addition to passwords for user authentication. In fact, I
In early 2007, PayPal (then part of the same company as eBay) began offering its hardware token for a one-time $5 fee, and at the time the company was among very few that were pushing this second-factor (something you have) in addition to passwords for user authentication. In fact, I