In the wake of megabreaches at some of the Internet’s most-recognized destinations, don’t be surprised if you receive password reset requests from numerous companies that didn’t experience a breach: Some big name companies — including Facebook and Netflix — are in the habit of combing through huge data leak troves for credentials that match those of their customers and then forcing a password reset for those users.
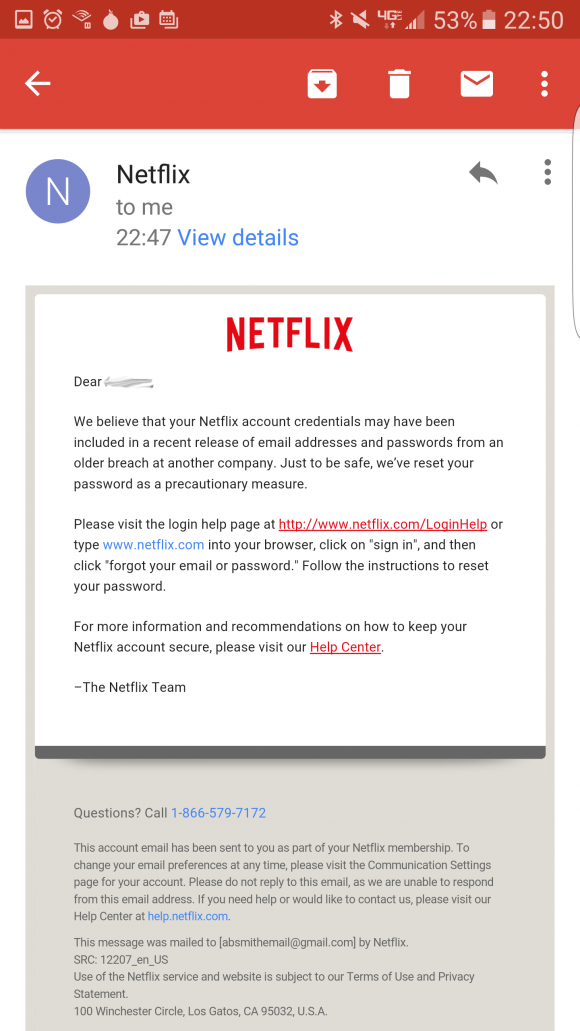
Netflix sent out notices to customers who re-used their Netflix password at other sites that were hacked. This notice was shared by a reader who had re-used his Netflix password at one of the breached companies.
Netflix.com, for example, sent out a notification late last week to users who made the mistake of re-using their Netflix password at Linkedin, Tumblr or MySpace. All of three of those breaches are years old, but the scope of the intrusions (more than a half billion usernames and passwords leaked in total) only became apparent recently when the credentials were posted online at various sites and services.
“We believe your Netflix account credentials may have been included in a recent release of email addresses and passwords from an older breach at another company,” the message from Neflix reads. “Just to be safe, we’ve reset your password as a precautionary measure.”
The missive goes on to urge recipients to visit Netflix.com and click the “forgot your email or password” link to reset their passwords.
Netflix is taking this step because it knows from experience that cybercriminals will be using the credentials leaked from Tumblr, MySpace and LinkedIn to see if they work on a variety of third-party sites (including Netflix).
As I wrote last year in the aftermath of the AshleyMadison breach that exposed tens of millions of user credentials, Netflix’s forensics team has been using a tool that the company released in 2014 called Scumblr, which scours high-profile sites for specific terms and data.
Facebook also has been known to mine data leaked in major external password breaches for any signs that users are re-using their passwords at the hacked entity. After at a breach discovered at Adobe in 2013 exposed tens of millions Adobe customer credentials, Facebook scoured the leaked Adobe password data for credential recycling among its users.
The last time I wrote about this preemptive security measure, many readers seem to have hastily and erroneously concluded that whichever company is doing the alerting doesn’t properly secure its users passwords if it can simply compare them in plain text to leaked passwords that have already been worked out.
What’s going on here is that Facebook, Netflix, or any other company who wants to can take a corpus of leaked passwords that have already been guessed or cracked and simply hash those passwords with whatever one-way hashing mechanism(s) they use internally. After that, it’s just a matter of finding any overlapping email addresses that use the same password.

Message that Facebook has used in the past to alert users who have re-used their Facebook passwords at other breached sites.
from
http://redirect.viglink.com?u=http%3A%2F%2Fkrebsonsecurity.com%2F2016%2F06%2Fpassword-re-user-get-to-get-busy%2F&key=ddaed8f51db7bb1330a6f6de768a69b8
No comments:
Post a Comment