The U.S. Secret Service is warning financial institutions about a recent uptick in a form of ATM skimming that involves cutting cupcake-sized holes in a cash machine and then using a combination of magnets and medical devices to siphon customer account data directly from the card reader inside the ATM.
According to a non-public alert distributed to banks this week and shared with KrebsOnSecurity by a financial industry source, the Secret Service has received multiple reports about a complex form of skimming that often takes thieves days to implement.
This type of attack, sometimes called ATM “wiretapping” or “eavesdropping,” starts when thieves use a drill to make a relatively large hole in the front of a cash machine. The hole is then concealed by a metal faceplate, or perhaps a decal featuring the bank’s logo or boilerplate instructions on how to use the ATM.

A thin metal faceplate is often used to conceal the hole drilled into the front of the ATM. The PIN pad shield pictured here is equipped with a hidden spy camera.
Skimmer thieves will fish the card skimming device through the hole and attach it to the internal card reader via a magnet.
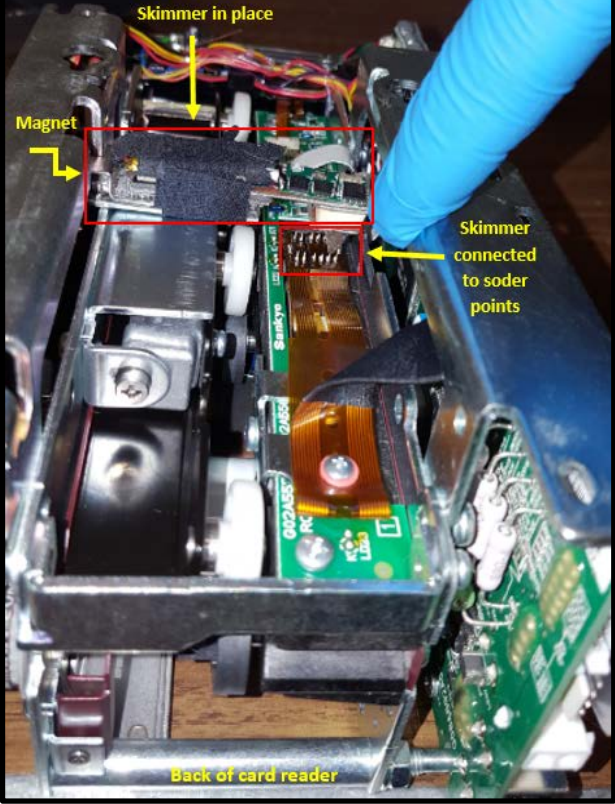
Thieves often use a magnet to secure their card skimmer in place above the ATM’s internal card reader. Image: U.S. Secret Service.
Very often the fraudsters will be assisted in the skimmer installation by an endoscope, a slender, flexible instrument traditionally used in medicine to give physicians a look inside the human body. By connecting a USB-based endoscope to his smart phone, the intruder can then peek inside the ATM and ensure that his skimmer is correctly attached to the card reader.

The Secret Service says once the skimmer is in place and the hole patched by a metal plate or plastic decal, the skimmer thieves often will wait a day or so to attach the pinhole camera. “The delay is believed to take place to ensure that vibrations from the drilling didn’t trigger an alarm from anti-skimming technology,” the alert reads.
When the suspect is satisfied that his drilling and mucking around inside the cash machine hasn’t set off any internal alarms, he returns to finish the job by retrofitting the ATM with a hidden camera. Often this is a false fascia directly in front of or above the PIN pad, recording each victim entering his or her PIN in a time-stamped video.
In other cases, the thieves may replace the PIN pad security shield on the ATM with a replica that includes a hidden pinhole camera, tucking the camera components behind the cut hole and fishing the camera wiring and battery through the hole drilled in the front of the machine.

The image on the left shows the spy camera guts and battery hidden behind the hole (this view is from the inside of the ATM, and the card reader is on the left). The image on the right shows a counterfeit PIN pad shield equipped with a hidden camera that is wired to the taped components pictured in the left image.
It’s difficult to cite all of the Secret Service’s report without giving thieves a precise blueprint on how to conduct these attacks. But I will say that several sources who spend a great deal of time monitoring cybercrime forums and communications have recently shared multiple how-to documents apparently making the rounds that lay out in painstaking detail how to execute these wiretapping attacks. So that knowledge is definitely being shared more widely in the criminal community now.
Overall, it’s getting tougher to spot ATM skimming devices, many of which are designed to be embedded inside various ATM components (e.g., insert skimmers). It’s best to focus instead on protecting your own physical security while at the cash machine. If you visit an ATM that looks strange, tampered with, or out of place, try to find another machine. Use only ATMs in public, well-lit areas, and avoid those in secluded spots.
Most importantly, cover the PIN pad with your hand when entering your PIN: That way, even if the thieves somehow skim your card, there is less chance that they will be able to snag your PIN as well. You’d be amazed at how many people fail to take this basic precaution.
Sure, there is still a chance that thieves could use a PIN-pad overlay device to capture your PIN, but in my experience these are far less common than hidden cameras (and quite a bit more costly for thieves who aren’t making their own skimmers). Done properly, covering the PIN pad with your hand could even block hidden cameras like those embedded in the phony PIN pad security shield pictured above.
from
https://krebsonsecurity.com/2018/09/secret-service-warns-of-surge-in-atm-wiretapping-attacks/
No comments:
Post a Comment