Online advertising firm Sizmek Inc. [NASDAQ: SZMK] says it is investigating a security incident in which a hacker was reselling access to a user account with the ability to modify ads and analytics for a number of big-name advertisers.
In a recent posting to a Russian-language cybercrime forum, an individual who’s been known to sell access to hacked online accounts kicked off an auction for “the admin panel of a big American ad platform.”
“You can add new users to the ad system, edit existing ones and ad offers,” the seller wrote. The starting bid was $800.
The seller included several screen shots of the ad company’s user panel. A few minutes on LinkedIn showed that many of these people are current or former employees of Sizmek.
The seller also shared a screenshot of the ad network’s Alexa site rankings:
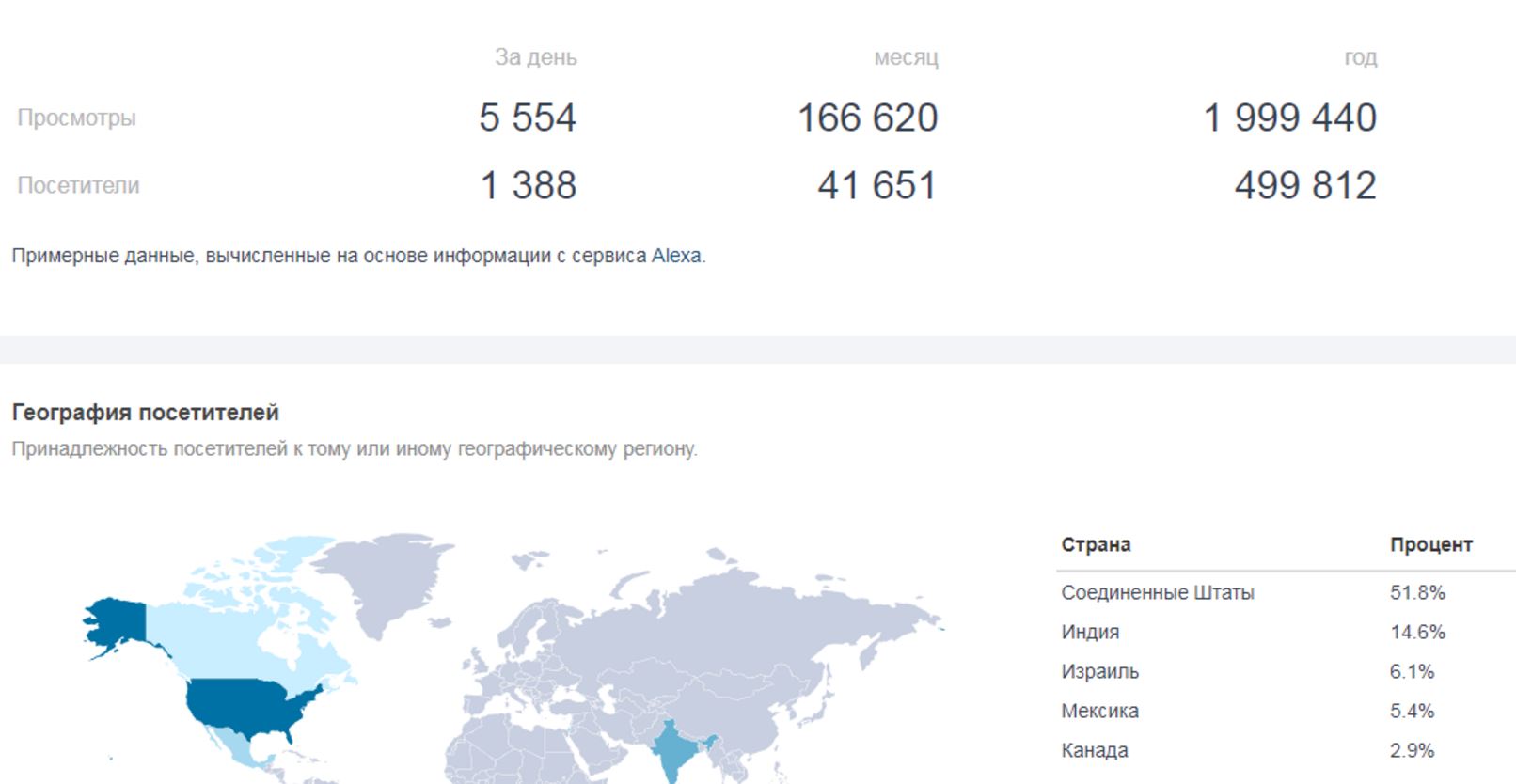
A screenshot of the Alexa ranking for the “big American ad network,” access to which was sold on a cybercrime forum.
I checked Sizmek’s Alexa page and at the time it almost mirrored the statistics shown in the screenshot above. Sizmek’s own marketing boilerplate says the company operates its ad platform in more than 70 countries, connecting more than 20,000 advertisers and 3,600 agencies to audiences around the world. The company is listed by market analysis firm Datanyze.com as the world third-largest ad server network.
After reaching out to a number of folks at Sizmek, I heard back from George Pappachen, the company’s general counsel.
Pappachen said the account being resold on the dark web is a regular user account (not a all-powerful administrator account, despite the seller’s claim) for its Sizmek Advertising Suite (SAS). Pappachen described Sizmek’s SAS product line as “a sizable and important one” for the company and a relatively new platform that has hundreds of users.
He acknowledged that the purloined account had the ability to add or modify the advertising creatives that get run on customer ad campaigns. And Sizmek is used in ad campaigns for some of the biggest brands out there. Some of the companies shown in the screenshot of the panel shared by the dark web seller include PR firm Fleishman-Hillard, media giants Fox Broadcasting, Gannett, and Hearst Digital, as well as Kohler, and Pandora.
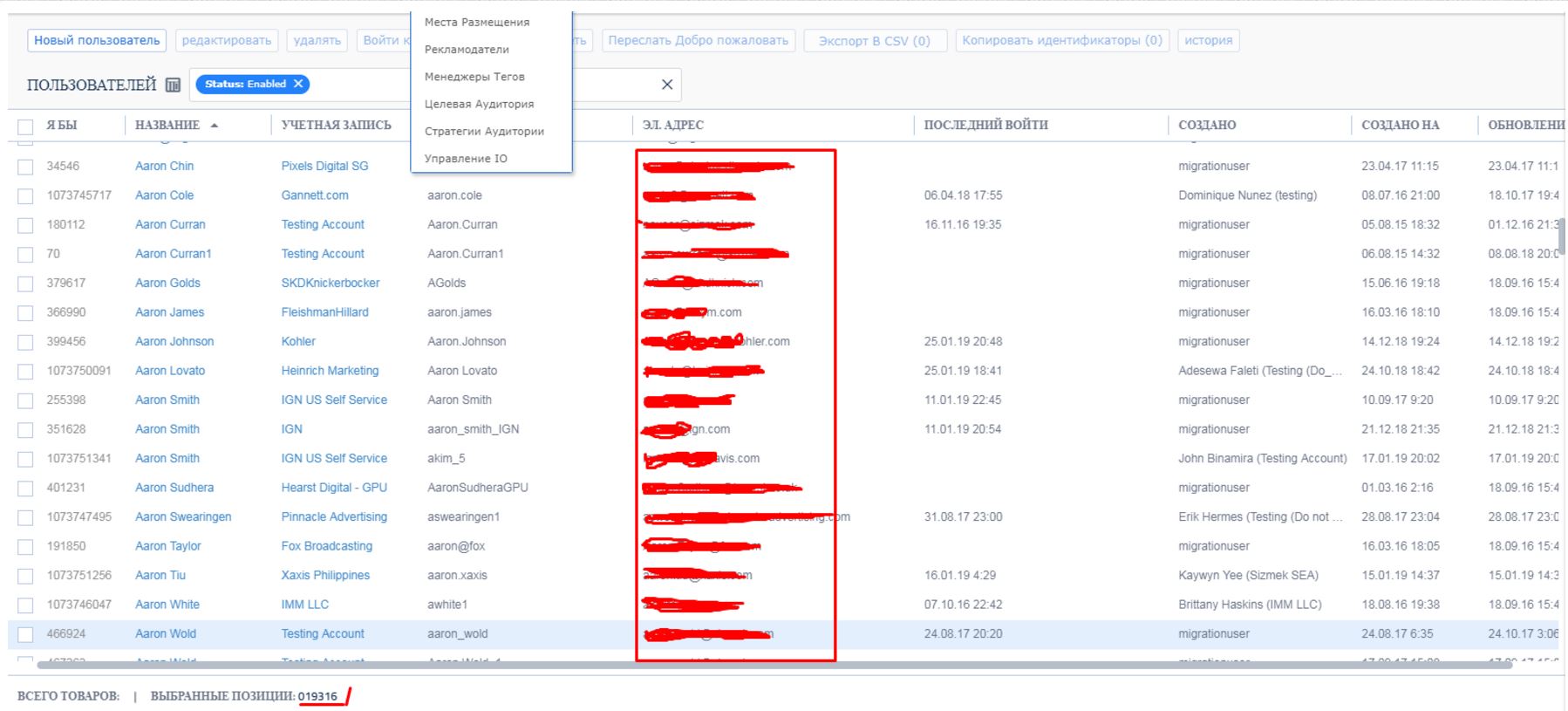
A screenshot shared by the dark web seller. Portions of this panel — access to a Sizmek user account — was likely translated by the Chrome Web browser, which has a built-in page translate function. As seen here, that function tends to translate items in the frame of the panel, but it leaves untouched the data inside those frames.
Crooks who exploited this access could hijack existing ad campaigns running on some of the world’s top online properties, by inserting malicious scripts into the HTML code of ads that run on popular sites. Or they could hijack referral commissions destined for others and otherwise siphon ad profits from the system.
“Or someone who is looking to sabotage our systems in a bigger way or allow malicious code to enter our systems,” Pappachen offered.
Pappachen said Sizmek forced a password reset on all internal employees (“a few hundred”), and that the company is scrubbing its SAS user database for departed employees, partners and vendors whose accounts may have been hijacked.
“We’re now doing some level of screening to see if there’s been any kind of intrusion we can detect,” Pappachen said. “It seemed like [the screenshots were accounts from] past employees. I think there were even a couple of vendors that had access to the system previously.”
The Sizmek incident carries a few lessons. For starters, it seems like an awful lot of people at Sizmek had access to sensitive controls and data a good deal longer than they should have. User inventory and management is a sometimes painful but very necessary ongoing security process at any mature organization.
Best practices in this space call for actively monitoring all accounts — users and admins — for signs of misuse or unauthorized access. And when employees or vendors sever business ties, terminate their access immediately.
Pappachen asked KrebsOnSecurity what else could have prevented this. I suggested some form of mobile-based multi-factor authentication option would prevent stolen credentials from turning into instant access. He said the company does use app/mobile based authentication for several of its new products and some internal programs, but allowed that “the legacy ones probably did not have this feature.”
PASSWORD SPRAYING

It’s not clear how this miscreant got access to Sizmek’s systems. But it is clear that attackers have moved rapidly of late toward targeting employees at key roles in companies they’d like to infiltrate, and they’re automating the guessing of passwords for employee accounts. One popular version of this attack involves what’s known as “password spraying,” which attempts to access a large number of accounts (usernames/email addresses) with a few commonly used passwords.
There are technologies like CAPTCHAs — requiring the user to solve an image challenge or retype squiggly letters — which try to weed out automated bot programs from humans. Then again, password spraying attacks often are conducted “low and slow” to help evade these types of bot challenges.
Password spraying was suspected in a compromise reported last week at Citrix, which said it heard from the FBI on March 6 that attackers had successfully compromised multiple Citrix employee accounts. A little-known security company Resecurity claimed it had evidence that Iranian hackers were responsible, had been in Citrix’s network for years, and had offloaded terabytes of data.
Resecurity drew criticism from many in the security community for not sharing enough evidence of the attacks. But earlier this week the company updated its blog post to include several Internet addresses and proxies it says the attackers used in the Citrix campaign. The update stated the attackers had gained access to nearly 32,000 Citrix accounts through password spraying.
Resecurity also presented evidence that it notified Citrix of the breach as early as Dec. 28, 2018. Citrix initially denied that claim, but has since acknowledged that it did receive a notification from Resecurity on Dec. 28. Citrix has declined to comment further beyond saying it is still investigating the matter.
BRUTE-FORCE LIGHT
 If anything, password spraying is a fairly crude, if sometimes marginally effective attack tool. But what we’ve started to see more of over the past year has been what one might call “brute-force light” attacks on accounts. A source who has visibility into a botnet of Internet of Things devices that is being mostly used for credential stuffing attacks said he’s seeing the attackers use distributed, hacked systems like routers, security cameras and digital video recorders to anonymize their repeated queries.
If anything, password spraying is a fairly crude, if sometimes marginally effective attack tool. But what we’ve started to see more of over the past year has been what one might call “brute-force light” attacks on accounts. A source who has visibility into a botnet of Internet of Things devices that is being mostly used for credential stuffing attacks said he’s seeing the attackers use distributed, hacked systems like routers, security cameras and digital video recorders to anonymize their repeated queries.
This source noticed that the automated system used by the IoT botmasters typically will try several dozen variations on a password that each target had previously used at another site — adding a “1” or an exclamation point at the end of a password, or capitalizing the first letter of whole words in previous passwords, and so on.
The idea behind this method to snare not only users who are wholesale re-using the same password across multiple sites, but to also catch users who may just be re-using slight variations on the same password.
This form of credential stuffing is brilliant from the attacker’s perspective because it probably nets him quite a few more correct guesses than normal password spraying techniques.
It’s also smart because it borrows from human nature. Let’s say your average password re-user is in the habit of recycling the password “monkeybutt.” But then he gets to a site that wants him to use capitalization in his password to create an account. So what does this user pick? Yes, “Monkeybutt.” Or “Monkeybutt1”. You get the picture.
There’s an old saying in security: “Everyone gets penetration tested, whether or not they pay someone for the pleasure.” It’s kind of like that with companies and their users and passwords. How would your organization hold up to a password spraying or brute-force light attack? If you don’t know, you should probably find out, and then act on the results accordingly. I guarantee you the bad guys are going to find out even if you don’t.
from
https://krebsonsecurity.com/2019/03/ad-network-sizmek-probes-account-breach/
No comments:
Post a Comment