Crooks who deploy skimming devices made to steal payment card details from fuel station pumps don’t just target filling stations at random: They tend to focus on those that neglect to deploy various tools designed to minimize such scams, including security cameras, non-standard pump locks and tamper-proof security tape. But don’t take my word for it: Here’s a look at fuel station compromises in 2016 as documented by the state of Arizona, which has seen a dramatic spike in fuel skimming attacks over the past year.
KrebsOnSecurity examined nearly nine months worth of pump skimming incidents in Arizona, where officials say they’ve documented more skimming attacks in the month of August 2016 alone than in all of 2015 combined.
With each incident, the Arizona Department of Agriculture’s Weights and Measures Services Division files a report detailing whether victim fuel station owners had observed industry best practices leading up to the hacks. As we can see from the interactive story map KrebsOnSecurity created below, the vast majority of compromised filling stations failed to deploy security cameras, and/or tamper-evident seals on the pumps.
Fewer still had changed the factory-default locks on their pumps, meaning thieves armed with a handful of master keys were free to unlock the pumps and install skimming devices at will.
These security report cards for fuel station owners aren’t complete assessments by any means. Some contain scant details about the above-mentioned precautionary measures, while other reports painstakingly document such information — complete with multiple photos of the skimming devices. Regardless, the data available show a clear trend of fraudsters targeting owners and operators that flout basic security best practices.
Indeed, the data assembled here suggests that skimmer thieves favor off-brand filling stations and target pumps furthest from the station/closest to the street. Also, all but three of the 35 incidents included in this report targeted fuel dispensers made by one manufacturer: Gilbarco — probably because the skimmer thieves responsible were armed with a master key for Gilbarco pumps.
In only one documented skimming incident did the station owner report having used non-standard pump locks. In some cases, the same filling station was hit with separate skimming attacks just a few months apart.
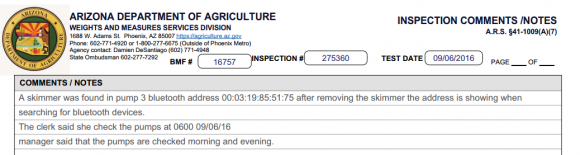
A portion of the incident report for the Bluetooth skimmers found at a gas station in Phoenix on Sept. 6, 2016
Investigators also appear to be increasingly finding pump skimmers that employ Bluetooth wireless technology. Bluetooth-based skimmers allow thieves to collect stolen card data merely by pulling up to a pump and downloading it with a Bluetooth-enabled laptop or mobile device (as opposed to taking the risk of re-opening the pumps to retrieve the siphoned card data).
A review of the locations of the skimmed stations suggests that skimmer scammers prefer poorly secured stations that are quite close to a major highway, no doubt so that they get away from the station relatively quickly after the skimmers are planted. It’s unclear whether the skimming attacks documented here are the work of one or multiple scammers or gangs, but the activity pretty clearly shows a focus on stations directly off the main arteries from Phoenix on down to Tuscon.
In some of the images in the slideshow above, it may be difficult to readily tell among the jumble of wires which bit is the skimmer. When in doubt, look for an area wrapped in black or grey colored electrical tape, which seems to be found in nearly all of these pump skimming attacks.
Arizona is almost certainly a microcosm of pump skimming activity going on nationally. Last year, KrebsOnSecurity ran an in-depth piece profiling a U.S. Secret Service task force that’s been battling a surge in pump skimming scams perpetrated by organized crime gangs in and around Los Angeles. Other stories on pump skimmers can be found in this search link.
Consumers should remember that they’re not liable for fraudulent charges on their credit or debit cards, but they still have to report the phony transactions. There is no substitute for keeping a close eye on your card statements. Also, use credit cards instead of debit cards at the pump; having your checking account emptied of cash while your bank sorts out the situation can be a huge hassle and create secondary problems (bounced checks, for instance).
I realize that the project above — made with the free StoryMap tool from Northwestern University’s Knight Lab — may be difficult to view comfortably within the confines of this blog. Here’s a direct link to the full map and timeline.
from
https://krebsonsecurity.com/2016/09/inside-arizonas-pump-skimmer-scourge/
No comments:
Post a Comment