I shared a meal not long ago with a source who works at a financial services company. The subject of ransomware came up and he told me that a server in his company had recently been infected with a particularly nasty strain that spread to several systems before the outbreak was quarantined. He said the folks in finance didn’t bat an eyelash when asked to authorize several payments of $600 to satisfy the Bitcoin ransom demanded by the intruders: After all, my source confessed, the data on one of the infected systems was worth millions — possibly tens of millions — of dollars, but for whatever reason the company didn’t have backups of it.
This anecdote has haunted me because it speaks volumes about what we can likely expect in the very near future from ransomware — malicious software that scrambles all files on an infected computer with strong encryption, and then requires payment from the victim to recover them.
What we can expect is not only more targeted and destructive attacks, but also ransom demands that vary based on the attacker’s estimation of the value of the data being held hostage and/or the ability of the victim to pay some approximation of what it might be worth.
In an alert published today, the U.S. Federal Bureau of Investigation (FBI) warned that recent ransomware variants have targeted and compromised vulnerable business servers (rather than individual users) to identify and target hosts, thereby multiplying the number of potential infected servers and devices on a network.
“Actors engaging in this targeting strategy are also charging ransoms based on the number of host (or servers) infected,” the FBI warned. “Additionally, recent victims who have been infected with these types of ransomware variants have not been provided the decryption keys for all their files after paying the ransom, and some have been extorted for even more money after payment.”
According to the FBI, this recent technique of targeting host servers and systems “could translate into victims paying more to get their decryption keys, a prolonged recovery time, and the possibility that victims will not obtain full decryption of their files.”
Today there are dozens of ransomware strains, most of which are sold on underground forums as crimeware packages — with new families emerging regularly. These kits typically include a point-and-click software interface for selecting various options that the ransom installer may employ, as well as instructions that tell the malware where to direct the victim to pay the ransom. Some kits even bundle the HTML code needed to set up the Web site that users will need to visit to pay and recover their files.
To some degree, a variance in ransom demands based on the victim’s perceived relative wealth is already at work. Lawrence Abrams, owner of the tech-help site BleepingComputer, said his analysis of multiple ransomware kits and control channels that were compromised by security professionals indicate that these kits usually include default suggested ransom amounts that vary depending on the geographic location of the victim.
“People behind these scams seem to be setting different rates for different countries,” Abrams said. “Victims in the U.S. generally pay more than people in, say, Spain. There was one [kit] we looked at recently that showed while victims in the U.S. were charged $200 in Bitcoin, victims in Italy were asked for just $20 worth of Bitcoin by default.”
In early 2016, a new ransomware variant dubbed “Samsam” (PDF) was observed targeting businesses running outdated versions of Red Hat‘s JBoss enterprise products. When companies were hacked and infected with Samsam, Abrams said, they received custom ransom notes with varying ransom demands.
“When these companies were hacked, they each got custom notes with very different ransom demands that were much higher than the usual amount,” Abrams said. “These were very targeted.”
Which brings up the other coming shift with ransomware: More targeted ransom attacks. For the time being, most ransomware incursions are instead the result of opportunistic malware infections. The first common distribution method is spamming the ransomware installer out to millions of email addresses, disguising it as a legitimate file such as an invoice.
More well-heeled attackers may instead or also choose to spread ransomware using “exploit kits,” a separate crimeware-as-a-service product that is stitched into hacked or malicious Web sites and lying in wait for someone to visit with a browser that is not up to date with the latest security patches (either for the browser itself or for a myriad of browser plugins like Adobe Flash or Adobe Reader).
But Abrams said that’s bound to change, and that the more targeted attacks are likely to come from individual hackers who can’t afford to spend thousands of dollars a month renting exploit kits.
“If you throw your malware into a good exploit kit, you can achieve a fairly wide distribution of it in a short amount of time,” Abrams said. “The only problem is the good kits are very expensive and can cost upwards of $4,000 per month. Right now, most of these guys are just throwing the ransomware up in the air and wherever it lands is who they’re targeting. But that’s going to change, and these guys are going to start more aggressively targeting really data intensive organizations like medical practices and law and architectural firms.”
Earlier this year, experts began noticing that ransomware purveyors appeared to be targeting hospitals — organizations that are extremely data-intensive and heavily reliant on instant access to patient records. Indeed, the above-mentioned SamSAM ransomware family is thought to be targeting healthcare firms.
According to a new report by Intel Security, the healthcare sector is experiencing over 20 data loss incidents per day related to ransomware attacks. The company said it identified almost $100,000 in payments from hospital ransomware victims to specific bitcoin accounts so far in 2016.
RUSSIAN ROULETTE
An equally disturbing trend in ransomware is the incidence of new strains which include the ability to randomly delete an encrypted file from the victim’s machine at some predefined interval –and to continue doing so unless and until the ransom demand is paid or there are no more files to destroy.
Abrams said the a ransomware variant known as “Jigsaw” debuted this capability in April 2016. Jigsaw also penalized victims who tried to reboot their computer in an effort to rid the machine of the infection, by randomly deleting 1,000 encrypted files for each reboot.
“Basically, what it would do is show a two hour countdown clock, and when that clock got to zero it would delete a random encrypted file,” Abrams said. “And then every hour after that it would double the number of files it deleted unless you paid.”
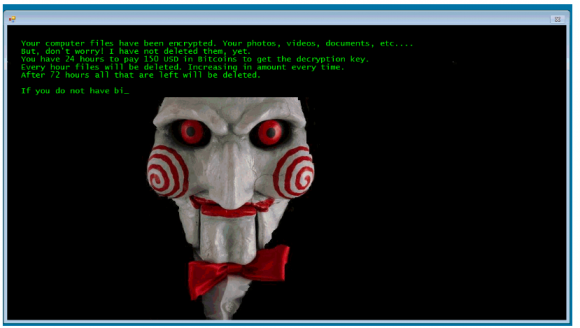
Part of the ransom note left behind by Jigsaw. Image: Bleepingcomputer.com
Abrams said this same Russian Roulette feature recently has shown up in other ransomware strains, including one called “Stampado” and another dubbed “Philadelphia.”
“Philadelphia has a similar feature where [one] can specify how many files it deletes and how often,” he said.
Most ransomware variants have used some version of the countdown clock, with victims most often being told they have 72 hours to pay the ransom or else kiss their files goodbye forever. In practice, however, the people behind these schemes are usually happy to extend that deadline, but the ransom demands almost invariably increase significantly at that point.
The introduction of a destructive element tied to a countdown clock is especially worrisome given how difficult it can be for the unlearned to obtain the virtual Bitcoin currency needed to pay the ransom, Abrams said.
“I had an architectural firm reach out to me, and they’d decided to pay the ransom,” he said. “So I helped my contact there figure out how to create an account at Coinbase.com and get funds into there, but the whole process took almost a week.”
Hoping to get access to his files more immediately, Abrams’ contact at the architectural firm inquired about more speedy payment options. Abrams told him about localbitcoins.com, which helps people meet in person to exchange bitcoins for cash. In the end, however, the contact wasn’t comfortable with this option.
“It’s not hard to see why,” he said. “Some of the exchangers on there have crazy demands, like ‘Meet me at the local Starbucks, and absolutely no phones!’ It really sort of feels like a drug deal.”
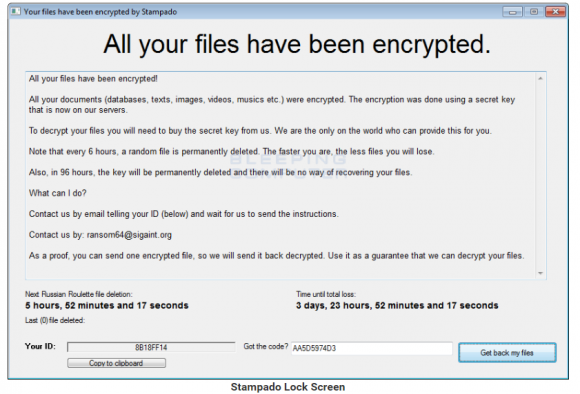
The ransom demand left by Stampado. Image: Bleepingcomputer.com
HOW TO PREVENT ATTACKS & WHAT TO DO IF YOU’RE A VICTIM
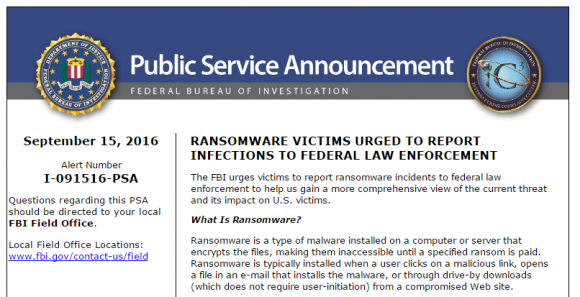
In its alert published today, the FBI urged victims of ransomware incidents to report the crimes to federal law enforcement to help the government “gain a more comprehensive view of the current threat and its impact on U.S. victims.”
Specifically, the FBI is asking victims to report the date of infection; the ransomware variant; how the infection occurred; the requested ransom amount; the actors Bitcoin wallet address; the ransom amount paid (if any); the overall losses associated with the ransomware infection; and a victim impact statement.
Previous media reports have quoted an FBI agent saying that the agency condones paying such ransom demands. But today’s plea from the feds to ransomware victims is unequivocal on this point:
“The FBI does not support paying a ransom to the adversary,” the agency advised. “Paying a ransom does not guarantee the victim will regain access to their data; in fact, some individuals or organizations are never provided with decryption keys after paying a ransom.”
What can businesses do to lessen the chances of becoming the next ransomware victim? The FBI has the following tips:
- Regularly back up data and verify the integrity of those backups. Backups are critical in ransomware incidents; if you are infected, backups may be the best way to recover your critical data.
- Secure your backups. Ensure backups are not connected to the computers and networks they are backing up. Examples might include securing backups in the cloud or physically storing them offline. It should be noted, some instances of ransomware have the capability to lock cloud-based backups when systems continuously back up in real-time, also known as persistent synchronization.
- Scrutinize links contained in e-mails and do not open attachments included in unsolicited e-mails.
- Only download software – especially free software – from sites you know and trust. When possible, verify the integrity of the software through a digital signature prior to execution.
- Ensure application patches for the operating system, software, and firmware are up to date, including Adobe Flash, Java, Web browsers, etc.
- Ensure anti-virus and anti-malware solutions are set to automatically update and regular scans are conducted.
- Disable macro scripts from files transmitted via e-mail. Consider using Office Viewer software to open Microsoft Office files transmitted via e-mail instead of full Office Suite applications.
- Implement software restrictions or other controls to prevent the execution of programs in common ransomware locations, such as temporary folders supporting popular Internet browsers, or compression/decompression programs, including those located in the AppData/LocalAppData folder.
Additional considerations for businesses include the following:
- Focus on awareness and training. Because end users are often targeted, employees should be made aware of the threat of ransomware, how it is delivered, and trained on information security principles and techniques.
- Patch all endpoint device operating systems, software, and firmware as vulnerabilities are discovered. This precaution can be made easier through a centralized patch management system.
- Manage the use of privileged accounts by implementing the principle of least privilege. No users should be assigned administrative access unless absolutely needed. Those with a need for administrator accounts should only use them when necessary; they should operate with standard user accounts at all other times.
- Configure access controls with least privilege in mind. If a user only needs to read specific files, he or she should not have write access to those files, directories, or shares.
- Use virtualized environments to execute operating system environments or specific programs.
- Categorize data based on organizational value, and implement physical/logical separation of networks and data for different organizational units. For example, sensitive research or business data should not reside on the same server and/or network segment as an organization’s e-mail environment.
- Require user interaction for end user applications communicating with Web sites uncategorized by the network proxy or firewall. Examples include requiring users to type in information or enter a password when the system communicates with an uncategorized Web site.
- Implement application whitelisting. Only allow systems to execute programs known and permitted by security policy.
from
http://redirect.viglink.com?u=http%3A%2F%2Fkrebsonsecurity.com%2F2016%2F09%2Fransomware-getting-more-targeted-expensive%2F&key=ddaed8f51db7bb1330a6f6de768a69b8

No comments:
Post a Comment