Last week, LifeLock and several other identity theft protection firms erroneously alerted their customers to a breach at cloud storage giant Dropbox.com — an incident that reportedly exposed some 73 million usernames and passwords. The only problem with that notification was that Dropbox didn’t have a breach; the data appears instead to have come from another breach revealed this week at social network Tumblr.
Today’s post examines some of the missteps that preceded this embarrassing and potentially brand-damaging “oops.” We’ll also explore the limits of automated threat intelligence gathering in an era of megabreaches like the ones revealed over the past week that exposed more than a half billion usernames and passwords stolen from Tumblr, MySpace and LinkedIn.
The credentials leaked in connection with breaches at those social networking sites were stolen years ago, but the full extent of the intrusions only became clear recently — when several huge archives of email addresses and hashed passwords from each service were posted to the dark web and to file-sharing sites.
Last week, a reader referred me to a post by a guy named Andrew on the dropbox.com help forum. Andrew said he’d just received alerts blasted out by two different credit monitoring firms that his dropbox credentials had been compromised and were found online (see screenshot below).
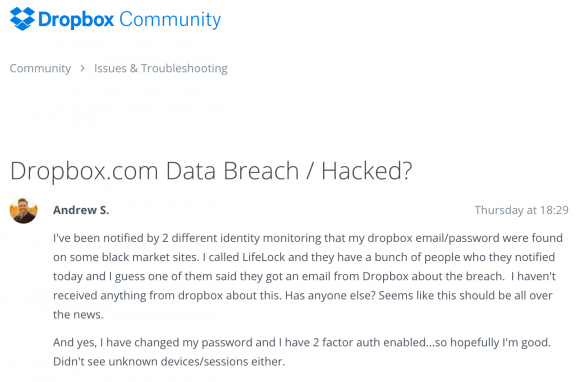
A user on the dropbox forum complains of receiving alerts from separate companies warning of a huge password breach at dropbox.com.
Here’s what LifeLock sent out on May 23, 2016 to many customers who pay for the company’s credential recovery services:
Alert Date: 05-23-2016
Alert Type: Monitoring
Alert Category: Internet-Black Market Website
**Member has received a File Sharing Network alert Email: *****
Password: ****************************************
Where your data was found: social media
Type of Compromise: breach
Breached Sector: business
Breached Site: www.dropbox.com
Breached Record Count: 73361477
Password Status: hashed
Severity: red|email,password
Site: www.dropbox.com
LifeLock said it got the alert data via an information sharing agreement with a third party threat intelligence service, but it declined to name the service that sent the false positive alert.
“We can confirm that we recently notified a small segment of LifeLock members that a version of their dropbox.com credentials were detected on the internet,” LifeLock said in a written statement provided to KrebsOnSecurity. “When we are notified about this type of information from a partner, it is usually a “list” that is being given away, traded or sold on the dark web. The safety and security of our members’ data is our highest priority. We are continuing to monitor for any activity within our source network. At this time, we recommend that these LifeLock members change their Dropbox password(s) as a precautionary measure.”
Dropbox says it didn’t have a breach, and if it had the company would be seeing huge amounts of account checking activity and other oddities going on right now. And that’s just not happening, they say.
“We have learned that LifeLock and MyIdCare.com are reporting that Dropbox account details of some of their customers are potentially compromised,” said Patrick Heim, head of trust and security at Dropbox. “An initial investigation into these reports has found no evidence of Dropbox accounts being impacted. We’re continuing to look into this issue and will update our users if we find evidence that Dropbox accounts have been impacted.”
FALSE POSITIVES?
After some digging, I learned that the bogus attribution of the Tumblr breach to Dropbox came from CSID, an identity monitoring firm that is in the midst of being acquired by credit bureau giant Experian.
Fascinated by anything related to security and false positives, I phoned Bryan Hjelm, vice president of product and marketing for CSID. Hjelm took issue with my classifying this as a threat intel false positive, since from CSID’s perspective the affected individual customers were in fact alerted that their credentials were compromised (just not their Dropbox credentials).
“Our mandate is to alert our client subscribers when we find their information on the darkweb,” Hjelm said. “Regardless of the source, this is compromised data that belongs to them.”
Hjelm acknowledged that CSID was “experiencing some reputational concerns” from Dropbox and others as a result of its breach mis-attribution, but he said the incident was the first time this kind of snafu has occurred for CSID.
I wanted to know exactly how this could have happened, so I asked Hjelm to describe what transpired in more detail. He told me that CSID relies on a number of sources online who have been accurate, early indicators of breaches past. One such actor — a sort of cyber gadfly best known by his hacker alias “w0rm” — had proven correct in previous posts on Twitter about new data breaches, Hjelm said.
In this case, w0rm posted to Twitter a link to download a file containing what he claimed were 100M records stolen from Dropbox. Perhaps one early sign that something didn’t quite add up is that the download he linked to as the Dropbox user file actually only included 73 million usernames and passwords.
In any case, CSID analysts couldn’t determine one way or the other whether it actually was Dropbox’s data. Nonetheless, they sent it out as such anyway, based on little more than w0rm’s say-so.
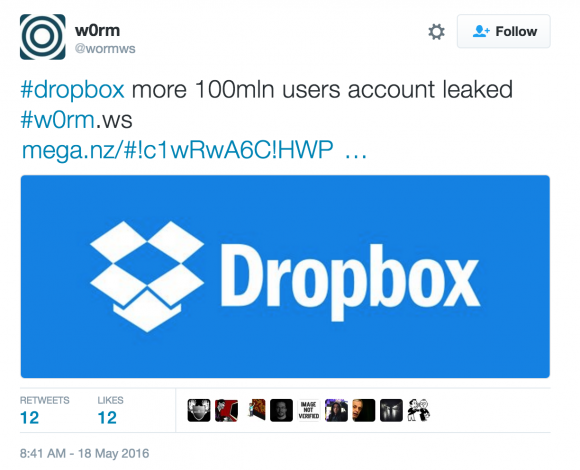
w0rm’s advertisement of the claimed dropbox credentials.
Hjelm said his analysts never test the validity of stolen credentials they’re harvesting from the dark web (i.e. they don’t try to log in using those credentials to see if they’re valid). But he said CSID may take steps such as attempting to crack some of the hashed passwords to see whether a preponderance of them point to a certain online merchant or social network.
In the LinkedIn breach involving more than 100,000 million stolen usernames and passwords, for example, investigators were able to connect a corpus of hashed passwords posted on a password cracking form to LinkedIn because a large number of users in the hashed password list had a password with some form of “linkedin” in it.
I asked CSID whether its researchers took the basic step of attempting to register accounts at the suspected breached service using the email addresses included in the supposed user data dump. As I discussed in the post How to Tell Data Leaks from Publicity Stunts, most online services do not allow two different user accounts to have the same email address, so attempting to sign up for an account using an email address in the claimed leak data is an effective way to test leak claims. If a large number of email addresses in the claimed leak list do not already have accounts associated with them at the allegedly breached Web site, the claim is almost certainly bogus.
Hjelm said CSID doesn’t currently use this rather manual technique, but that the company is open to suggestions about how to improve the accuracy of their breach victim attribution. He said CSID only started providing attribution information about a year ago because clients were demanding it.
Allison Nixon, a cybercrime researcher and director of security research at dark web monitoring firm Flashpoint, was the genesis of that aforementioned story about data leaks vs. publicity stunts. She’s done more research than anyone I know to date on ways to quickly tell whether a claimed breach is real, and how to source it. Nixon said automating threat intel only goes so far.
“In general, the skill of human skepticism performed today by threat intelligence experts is extremely difficult to automate,” Nixon said. “Even with advancements in cognitive and artificial intelligence technologies, humans will still and always be needed to validate the nuances associated with accurate intelligence. Security experts must be intimately involved in the fact checking process of threat intelligence, or otherwise, will run the risk of losing valuable time, resources and possibly even more, by validating false information perceived as accurate by automated technologies.”
Flashpoint found closer examination of the file that w0rm leaked maps back to a 2013 recycled breach at Tumblr.
There is no question w0rm has a history of sharing real dumps. But according to Flashpoint that reputation must be taken with a grain of salt because even though the dumps are real, they are usually publicly available yet are portrayed by w0rm as evidence of his hacking proficiency.
In short: The intended victim of guys like w0rm is probably other cybercriminals, but threat intel companies can get caught up in this as well.
Many readers have asked me to weigh in on reports of a possible breach at Teamviewer, a service that lets users share their desktops, audio chat and other applications with friends and contacts online. Teamviewer has so far denied experiencing a breach.
My guess is that a large number of Teamviewer users either re-used passwords at some of the social networking services whose usernames and hashed passwords were posted online this week, or they are Teamviewer users who unfortunately were caught up in the day-to-day churn of systems compromised through other malware. In any case, there is a lengthy thread on Reddit populated by Teamviewer users who mostly claim they didn’t re-use their Teamviewer password anywhere else.
It’s interesting to note that early versions of remote access Trojans like Zeus contained a Teamviewer-like component called “backconnect” that let the attackers use the systems much like Teamviewer enables its users. These days, however, cybercriminals often forgo that homegrown backconnect feature and rely instead on either equipping the victim with a Teamviewer account and/or hijacking the victim’s existing Teamviewer account credentials, and then exfiltrating stolen credentials and other data through a Teamviewer installation. Hence, a compromise of one’s Teamviewer account may indicate that the victim’s system already is compromised by sophisticated Windows-based malware.
For its part, Dropbox is using this opportunity to encourage users to beef up the security of their accounts. According to Dropbox’s Patrick Heim, less than one percent of the Dropbox user base is taking advantage of the company’s two-factor authentication feature, which makes it much harder for thieves and other ne’er-do-wells to use stolen passwords.
“In matters of security, we always suggest users take an abundance of caution and reset their passwords if they receive any notification of a potential compromise,” Heim said. “Dropbox strongly encourages individuals use strong and unique passwords for each service. We also encourage Dropbox users to enable two-factor authentication to further protect their account.”
I hope it goes without saying that re-using passwords across multiple sites that may hold personal information about you is an extermely bad idea. If you’re guilty of this apparently common practice, please change that. If you need some inspiration on this front, check out this post.
from
http://redirect.viglink.com?u=http%3A%2F%2Fkrebsonsecurity.com%2F2016%2F06%2Fdropbox-smeared-in-week-of-megabreaches%2F&key=ddaed8f51db7bb1330a6f6de768a69b8
No comments:
Post a Comment