For the second time in the past nine months, Google has inadvertently but nonetheless correctly helped to identify the source of a large credit card breach — by assigning a “This site may be hacked” warning beneath the search results for the Web site of a victimized merchant.
A little over a month ago, KrebsOnSecurity was contacted by multiple financial institutions whose anti-fraud teams were trying to trace the source of a great deal of fraud on cards that were all used at a handful of high-end restaurants around the country.
Two of those fraud teams shared a list of restaurants that all affected cardholders had visited recently. A bit of searching online showed that nearly all of those establishments were run by Select Restaurants Inc., a Cleveland, Ohio company that owns a number of well-known eateries nationwide, including Boston’s Top of the Hub; Parker’s Lighthouse in Long Beach, Calif.; the Rusty Scupper in Baltimore, Md.; Parkers Blue Ash Tavern in Cincinnati, Ohio; Parkers’ Restaurant & Bar in Downers Grove, Illinois; Winberie’s Restaurant & Bar with locations in Oak Park, Illinois and Princeton and Summit, New Jersey; and Black Powder Tavern in Valley Forge, PA.
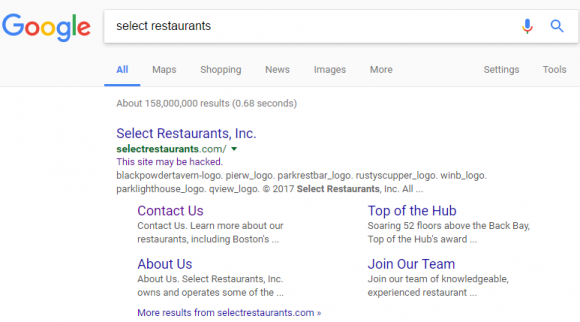
Google’s search listing for Select Restaurants, which indicates Google thinks this site may be hacked.
Knowing very little about this company at the time, I ran a Google search for it and noticed that Google believes the site may be hacked (it still carries this message). This generally means some portion of the site was compromised by scammers who are trying to abuse the site’s search engine rankings to beef up the rankings for “spammy” sites — such as those peddling counterfeit prescription drugs and designer handbags.
The “This site may be hacked” advisory is not quite as dire as Google’s “This site may harm your computer” warning — the latter usually means the site is actively trying to foist malware on the visitor’s computer. But in my experience it’s never a good sign when a business that accepts credit cards has one of these warnings attached to its search engine results.
Case in point: I experienced this exact scenario last summer as I was reporting out the details on the breach at CiCi’s Pizza chain. In researching that story, all signs were pointing to a point-of-sale (POS) terminal provider called Datapoint POS. Just like it did with Select Restaurants’s site, Google reported that Datapoint’s site appeared to be hacked.
Select Restaurants did not return messages seeking comment. But as with the breach at Cici’s Pizza chains, the breach involving Select Restaurant locations mentioned above appears to have been the result of an intrusion at the company’s POS vendor — Geneva, Ill. based 24×7 Hospitality Technology. 24×7 handles credit and debit card transactions for thousands of hotels and restaurants, including more than 200 Buffalo Wild Wings franchises nationwide.
On Feb. 14, 24/7 Hospitality sent a letter to customers warning that its systems recently were hacked by a “sophisticated network intrusion through a remote access application.” Translation: Someone guessed or phished the password that we use to remotely administer point-of-sale systems at its customer locations. 24×7 said the attackers subsequently executed the PoSeidon malware variant, which is designed to siphon card data when cashiers swipe credit cards at an infected cash register (for more on PoSeidon, check out POS Providers Feel Brunt of PoSeidon Malware).
KrebsOnSecurity obtained a copy of the letter (PDF) that 24/7 Hospitality CEO Todd Baker, Jr. sent to Select Restaurants. That missive said even though the intruders apparently had access to all of 24/7 customers’ payment systems, not all of those systems were logged into by the hackers. Alas, this was probably little consolation for Select Restaurants, because the letter then goes on to say that the breach involves all of the restaurants listed on Select’s Web site, and that the breach appears to have extended from late October 2016 to mid-January 2017.
ANALYSIS
From my perspective, organized crime gangs have so completely overrun the hospitality and restaurant point-of-sale systems here in the United States that I just assume my card may very well be compromised whenever I use it at a restaurant or hotel bar/eatery. I’ve received no fewer than three new credit cards over the past year, and I’d wager that in at least one of those cases I happened to have used the card at multiple merchants whose POS systems were hacked at the same time.
But no matter how many times I see it, it’s fascinating to watch this slow motion train wreck play out. Given how much risk and responsibility for protecting against these types of hacking incidents is spread so thinly across the entire industry, it’s little wonder that organized crime gangs have been picking off POS providers for Tier 3 and Tier 4 merchants with PoSeidon en masse in recent years.
I believe one big reason we keep seeing the restaurant and hospitality industry being taken to the cleaners by credit card thieves is that in virtually all of these incidents, the retailer or restaurant has no direct relationships to the banks which have issued the cards that will be run through their hacked POS systems. Rather, these small Tier 3 and Tier 4 merchants are usually buying merchant services off of a local systems integrator who often is in turn reselling access to a third-party payment processing company.
As a result, very often when these small chains or solitary restaurants get hit with PoSeidon, there is no record of a breach that is simple to follow from the breached merchant back to the bank which issued the cards used at those compromised merchants. It is only by numerous financial institutions experiencing fraud from the same restaurants and then comparing notes about possible POS vendors in common among these restaurants that banks and credit unions start to gain a clue about what’s happening and who exactly has been hacked.
But this takes a great deal of time, effort and trust. Meanwhile, the crooks are laughing all the way to the bank. Another reason I find all this fascinating is that the two main underground cybercrime shops that appear to be principally responsible for offloading cards stolen in these Tier 3 and Tier 4 merchant breaches involving PoSeidon — stores like Rescator and Briansdump — both abuse my likeness in their advertisements and on their home pages. Here’s Briansdump:
![An advertisement for the carding shop “briansdump[dot]ru” promotes “dumps from the legendary Brian Krebs.” Needless to say, this is not an endorsed site.](http://krebsonsecurity.com/wp-content/uploads/2017/03/briansdumps.png)
An advertisement for the carding shop “briansdump[dot]ru” promotes “dumps from the legendary Brian Krebs.” Needless to say, this is not an endorsed site.
The login page for Rescator, a major seller of credit and debit cards stolen in countless attacks targeting retailers, restaurants and hotels.
Point-of-sale malware has driven most of the major retail industry credit card breaches over the past two years, including intrusions at Target and Home Depot, as well as breaches at a ridiculous number of point-of-sale vendors. The malware sometimes is installed via hacked remote administration tools like LogMeIn; in other cases the malware is relayed via “spear-phishing” attacks that target company employees. Once the attackers have their malware loaded onto the point-of-sale devices, they can remotely capture data from each card swiped at that cash register.
Thieves can then sell that data to crooks who specialize in encoding the stolen data onto any card with a magnetic stripe, and using the cards to purchase high-priced electronics and gift cards from big-box stores like Target and Best Buy.
Readers should remember that they’re not liable for fraudulent charges on their credit or debit cards, but they still have to report the unauthorized transactions. There is no substitute for keeping a close eye on your card statements. Also, consider using credit cards instead of debit cards; having your checking account emptied of cash while your bank sorts out the situation can be a hassle and lead to secondary problems (bounced checks, for instance).
Finally, if your credit card is compromised, try not to lose sleep over it: The chances of your finding out how that card was compromised are extremely low. This story seeks to explain why.
from
https://krebsonsecurity.com/2017/03/google-points-to-another-pos-vendor-breach/

No comments:
Post a Comment