I cannot recall a previous data breach in which the breached company’s public outreach and response has been so haphazard and ill-conceived as the one coming right now from big-three credit bureau Equifax, which rather clumsily announced Thursday that an intrusion jeopardized Social security numbers and other information on 143 million Americans.
WEB SITE WOES
As noted in yesterday’s breaking story on this breach, the Web site that Equifax advertised as the place where concerned Americans could go to find out whether they were impacted by this breach — equifaxsecurity2017.com —
is completely broken at best, and little more than a stalling tactic or sham at worst.
In the early hours after the breach announcement, the site was being flagged by various browsers as a phishing threat. In some cases, people visiting the site were told they were not affected, only to find they received a different answer when they checked the site with the same information on their mobile phones.
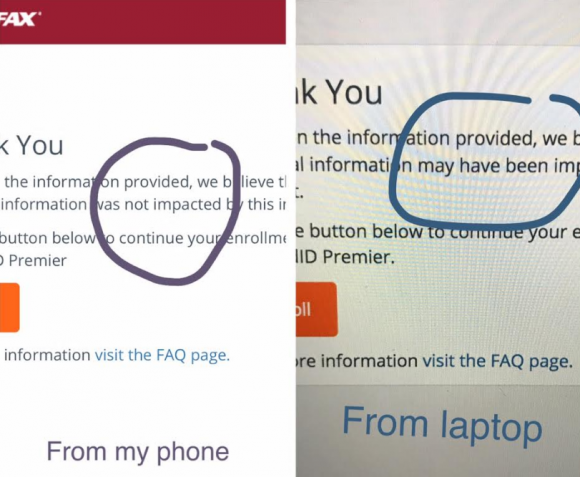
Others (myself included) received not a yes or no answer to the question of whether we were impacted, but instead a message that credit monitoring service we were eligible for was not available and to check back later in the month. The site asked users to enter their last name and last six digits of their SSN, but at the prompting of a reader’s comment I confirmed that just entering gibberish names and numbers produced the same result as the one I saw when I entered my real information: Come back on Sept. 13.
Who’s responsible for this debacle? Well, Equifax of course. But most large companies that can afford to do so hire outside public relations or disaster response firms to walk them through the safest ways to notify affected consumers. In this case, Equifax appears to have hired global PR firm Edelman PR.
What gives me this idea? Until just a couple of hours ago, the copy of WordPress installed at equifaxsecurity2017.com included a publicly accessible user database entry showing a user named “Edelman” was the first (and only?) user registered on the site.
Code that was publicly available on equifaxsecurity2017.com until very recently showed account information for an outside PR firm.
I reached out to Edelman for more information and will update this story when I hear from them.
EARLY WARNING?
In its breach disclosure Thursday, Equifax said it hired an outside computer security forensic firm to investigate as soon as it discovered unauthorized access to its Web site. ZDNet published a story Thursday saying that the outside firm was Alexandria, Va.-based Mandiant — a security firm bought by FireEye in 2014.
Interestingly, anyone who happened to have been monitoring look-alike domains for Equifax.com prior to yesterday’s breach announcement may have had an early clue about the upcoming announcement. One interesting domain that was registered on Sept. 5, 2017 is “equihax.com,” which according to domain registration records was purchased by an Alexandria, Va. resident named Brandan Schondorfer.
A quick Google search shows that Schondorfer works for Mandiant. Ray Watson, a cybersecurity researcher who messaged me this morning on Twitter about this curiosity, said it is likely that Mandiant has been registering domains that might by attractive to phishers hoping to take advantage of public attention to the breach and spoof Equifax’s domain.
Watson said it’s equally likely the equihax.com domain was registered to keep it out of the hands of people who may be looking for domain names they can use to lampoon Equifax for its breach. Schondorfer has not yet returned calls seeking comment.
EQUIFAX EXECS PULL GOLDEN PARACHUTES?
Bloomberg moved a story yesterday indicating that three top executives at Equifax sold millions of dollars worth of stock during the time between when the company says it discovered the breach and when it notified the public and investors.
Shares of Equifax’s stock on the New York Stock Exchange [NSYE:EFX] were down more than 13 percent at time of publication versus yesterday’s price.
The executives reportedly told Bloomberg they didn’t know about the breach when they sold their shares. A law firm in New York has already announced it is investigating potential insider trading claims against Equifax.
CLASS ACTION WAIVER?
Yesterday’s story here pointed out the gross conflict of interest in Equifax’s consumer remedy for this breach: Offering a year’s worth of free credit monitoring services to all Americans via its own in-house credit monitoring service.
This is particularly rich because a) why should anyone trust Equifax to do anything right security-wise after this debacle and b) these credit monitoring services typically hard-sell consumers to sign up for paid credit protection plans when the free coverage expires.

Verbiage from the terms of service from Equifax’s credit monitoring service TrustID Premier.
I have repeatedly urged readers to consider putting a security freeze on their accounts in lieu of or in addition to accepting these free credit monitoring offers, noting that credit monitoring services don’t protect you against identity theft (the most you can hope for is they alert you when ID thieves do steal your identity), while security freezes can prevent thieves from taking out new lines of credit in your name.
Several readers have written in to point out some legalese in the terms of service the Equifax requires all users to acknowledge before signing up for the service seems to include legal verbiage suggesting that those who do sign up for the free service will waive their rights to participate in future class action lawsuits against the company.
KrebsOnSecurity is still awaiting word from an actual lawyer who’s looking at this contract, but let me offer my own two cents on this. Equifax will almost certainly see itself the target of multiple class action lawsuits as a result of this breach, but there is no guarantee those lawsuits will go the distance and result in a monetary windfall for affected consumers.
Even when these cases do result in a win for the plaintiff class, it can take years. After KrebsOnSecurity broke the story in 2013 that Experian had given access to 200 million consumer records to Vietnamese man running an identity theft service, two different law firms filed class action suits against Experian.
That case was ultimately tossed out of federal court and remanded to state court, where it is ongoing. That case was filed in 2015.
To close out the subject of civil lawsuits as a way to hold companies accountable for sloppy security, class actions — even when successful — rarely result in much of a financial benefit for affected consumers (very often the “reward” is a gift card or two-digit dollar amount per victim), while greatly enriching law firms that file the suits.
It’s my view that these class action lawsuits serve principally to take the pressure off of lawmakers and regulators to do something that might actually prevent more sloppy security practices in the future for the victim culpable companies. And as I noted in yesterday’s story, the credit bureaus have shown themselves time and again to terribly unreliable stewards of sensitive consumer data: This time, the intruders were able to get in because Equifax apparently fell behind in patching its Internet-facing Web applications.
In May, KrebsOnSecurity reported that fraudsters exploited lax security at Equifax’s TALX payroll division, which provides online payroll, HR and tax services. In 2015, a breach at Experian jeopardized the personal data on at least 15 million consumers.
CAPITALIZING ON FEAR
Speaking of Experian, the company is now taking advantage of public fear over the breach — via hashtag #equifaxbreach, for example — to sign people up for their cleverly-named “CreditLock” subscription service (again, hat tip to @rayjwatson).
“When you have Experian Identity Theft Protection, you can instantly lock or unlock your Experian Credit File with the simple click of a button,” the ad enthuses. “Experian gives you instant access to your credit report.”
First off, all consumers have the legal right to instant access to their credit report via the Web site, annualcreditreport.com. This site, mandated by Congress, gives consumers the right to one free credit report from each of the three major bureaus (Equifax, Trans Union and Experian) every year.
Second, all consumers have a right to request that the bureaus “freeze” their credit files, which bars potential creditors or anyone else from viewing your credit history or credit file unless you thaw the freeze (temporarily or permanently).
I have made no secret of my disdain for the practice of companies offering credit monitoring in the wake of a data breach — especially in cases where the breach only involves credit card accounts, since credit monitoring services typically only look for new account fraud and do little or nothing to prevent fraud on existing consumer credit accounts.
Credit monitoring services rarely prevent identity thieves from stealing your identity. The most you can hope for from these services is that they will alert you as soon as someone does steal your identity. Also, the services can be useful in helping victims recover from ID theft.
My advice: Sign up for credit monitoring if you can (and you’re not holding out for a puny class action windfall) and then freeze your credit files at the major credit bureaus (it is generally not possible to sign up for credit monitoring services after a freeze is in place). Again, advice for how to file a freeze is available here.
Whether you are considering a freeze, credit monitoring, or a fraud alert (another, far less restrictive third option), please take a moment to read this story in its entirety. It includes a great deal of information that cannot be shared in a short column here.
from
https://krebsonsecurity.com/2017/09/equifax-breach-response-turns-dumpster-fire/
No comments:
Post a Comment