Fiserv, Inc., a major provider of technology services to financial institutions, just fixed a glaring weakness in its Web platform that exposed personal and financial details of countless customers across hundreds of bank Web sites, KrebsOnSecurity has learned.
Brookfield, Wisc.-based Fiserv [NASDAQ:FISV] is a Fortune 500 company with 24,000 employees and $5.7 billion in earnings last year. Its account and transaction processing systems power the Web sites for hundreds of financial institutions — mostly small community banks and credit unions.

Two weeks ago this author heard from security researcher Kristian Erik Hermansen, who said he’d discovered something curious while logged in to an account at a tiny local bank that uses Fiserv’s platform.
Hermansen had signed up to get email alerts any time a new transaction posted to his account, and he noticed the site assigned his alert a specific “event number.” Working on a hunch that these event numbers might be assigned sequentially and that other records might be available if requested directly, Hermansen requested the same page again but first edited the site’s code in his browser so that his event number was decremented by one digit.
In an instant, he could then view and edit alerts previously set up by another bank customer, and could see that customer’s email address, phone number and the last four digits of their bank account number.
Hermansen said a cybercriminal could abuse this access to enumerate all other accounts with activity alerts on file, and to add or delete phone numbers or email addresses to receive alerts about account transactions.
This would allow any customer of the bank to spy on the daily transaction activity of other customers, and perhaps even target customers who signed up for high minimum balance alerts (e.g., “alert me when the available balance goes below $5,000”).
“I shouldn’t be able to see this data,” Hermansen said. “Anytime you spend money that should be a private transaction between you and your bank, not available for everyone else to see.”
Hermansen said he told his bank about what he found, and that he tried unsuccessfully to get the attention of different Fiserv employees, including the company’s CEO via LinkedIn. But he wasn’t sure whether the flaw he found existed in all bank sites running on Fiserv’s ebanking platform, or just his bank’s installation.
Naturally, KrebsOnSecurity offered to help figure that out, and to get Fiserv’s attention, if warranted. Over the past week I signed up for accounts at two small local banks that each use Fiserv’s online banking platform.
In both cases I was able to replicate Hermansen’s findings and view email addresses, phone numbers, partial account numbers and alert details for other customers of each bank just by editing a single digit in a Web page request. I was relieved to find I could not use my online account access at one bank to view transaction alerts I’d set up at a different Fiserv affiliated bank.
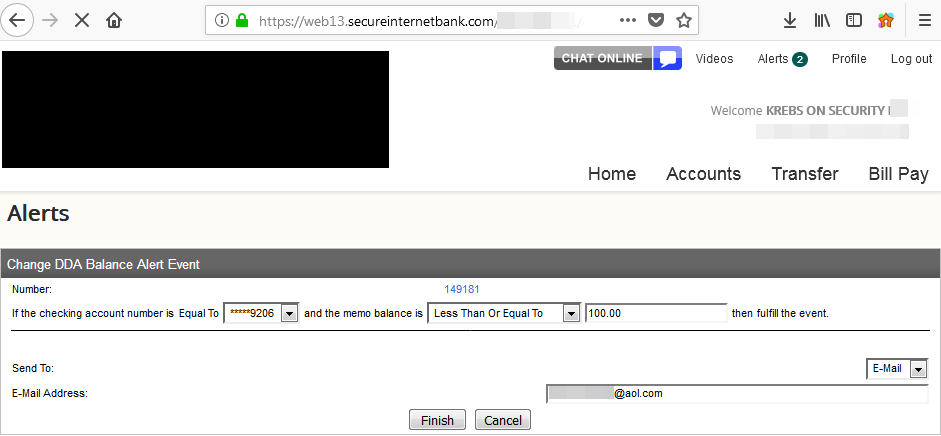
A single digit changed in a Web browser request caused someone else’s alerts to pop up in my account at this small local bank in Virginia.
But it was not difficult to find hundreds of other Fiserv-affiliated banks that would be just as vulnerable. If a bank is using Fiserv’s platform, it usually says so somewhere at the bottom of the bank’s home page. Another giveaway is that most of the bank sites using Fiserv display the same root domain name in the browser address bar after login: secureinternetbank.com.
Fiserv said in a statement that the problem stemmed from an issue with “a messaging solution available to a subset of online banking clients.” Fiserv declined to say exactly how many financial institutions may have been impacted overall. But experts tells KrebsOnSecurity that some 1,700 banks currently use Fiserv’s retail (consumer-focused) banking platform alone.
“Fiserv places a high priority on security, and we have responded accordingly,” Fiserv spokesperson Ann Cave said. “After receiving your email, we promptly engaged appropriate resources and worked around the clock to research and remediate the situation. We developed a security patch within 24 hours of receiving notification and deployed the patch to clients that utilize a hosted version of the solution. We will be deploying the patch this evening to clients that utilize an in-house version of the solution.”
This author confirmed that Fiserv no longer shows a sequential event number in their banking sites and has replaced them with a pseudo-random string.
Julie Conroy, research director with market analyst firm Aite Group, said the kinds of banks that use Fiserv’s platform mostly are those that can’t afford to build and maintain their own.
“These financial institutions use a core banking provider like Fiserv because they don’t have the wherewithal to do it on their own, so they’re really trusting Fiserv to do this on their behalf,” Conroy said. “This will not only reflect on Fiserv’s brand, but also it will impact customer’s perception about their small local bank, which is already struggling to compete with the larger, nationwide institutions.”
Allen Weinberg, partner and co-founder at Glenbrook Partners LLC, said the ability of fraudsters to edit account transaction alerts somewhat negates the value of these alerts in helping consumers fight fraud tied to their online banking accounts.
“If a fraudster can just turn off the alerts, there’s one less protection that consumers think they have,” Weinberg said. “I think consumers do rely in large part on these alerts to help them detect fraudulent activity.”
The weaknesses in Fiserv’s platform is what’s known as an “information disclosure” vulnerability. While these are among the most common types of security issues with Web sites, they are also perhaps the most preventable and easily fixed.
Nevertheless, disclosure flaws can be just as damaging to a company’s brand as other more severe types of security errors. Other notable security incidents involving recent information disclosure issues include a weakness at Panera Bread’s site that exposed tens of millions of customer records, and a bug in identity protection service LifeLock’s site that revealed email addresses for millions of customers.
from
https://krebsonsecurity.com/2018/08/fiserv-flaw-exposed-customer-data-at-hundreds-of-banks/
No comments:
Post a Comment