Prosecutors in Northern California have charged two men with using unauthorized SIM swaps to steal and extort money from victims. One of the individuals charged allegedly used a hacker nickname belonging to a key figure in the underground who’s built a solid reputation hijacking mobile phone numbers for profit.
According to indictments unsealed this week, Tucson, Ariz. resident Ahmad Wagaafe Hared and Matthew Gene Ditman of Las Vegas were part of a group that specialized in tricking or bribing representatives at the major wireless providers into giving them control over phone numbers belonging to people they later targeted for extortion and theft.
Investigators allege that between October 2016 and May 2018, Hared and Ditman grew proficient at SIM swapping, a complex form of mobile phone fraud that is often used to steal large amounts of cryptocurrencies and other items of value from victims.
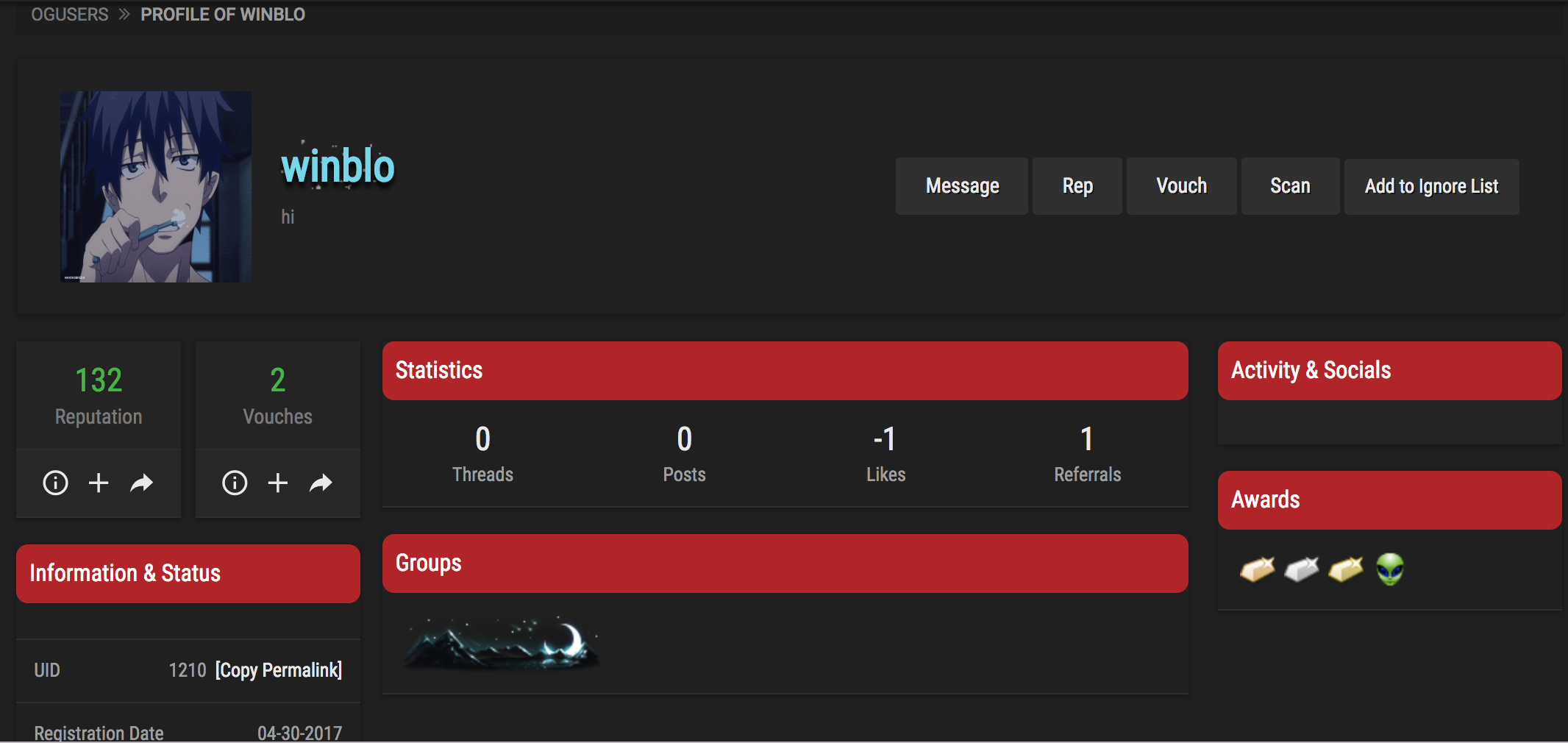
The Justice Department says Hared was better known to his co-conspirators as “winblo.” That nickname corresponds to an extremely active and at one time revered member of the forum ogusers[.]com, a marketplace for people who wish to sell highly prized social media account names — including short usernames at Twitter, Instagram and other sites that can fetch thousands of dollars apiece.
Winblo was an associate and business partner of another top Oguser member, a serial SIM swapper known to Oguser members as “Xzavyer.” In August 2018, authorities in California arrested a hacker by the same name — whose real name is Xzavyer Clemente Narvaez — charging him with identity theft, grand theft, and computer intrusion.Prosecutors allege Narvaez used the proceeds of his crimes (estimated at > $1 million in virtual currencies) to purchase luxury items, including a McLaren — a $200,000 high-performance sports car.
According to the indictments against Hared and Ditman, one of the men (the indictment doesn’t specify which) allegedly used his ill-gotten gains to purchase a BMW i8, an automobile that sells for about $150,000.
Investigators also say the two men stole approximately 40 bitcoins from their SIM swapping victims. That’s roughly $136,000 in today’s conversion, but it would have been substantially more in 2017 when the price of a single bitcoin reached nearly $20,000.
Interestingly, KrebsOnSecurity was contacted in 2018 by a California man who said he was SIM swapped by Winblo and several associates. That victim, who asked not to be identified for fear of reprisals, said his Verizon mobile number was SIM hijacked by Winblo and others who used that access to take over his Twitter and PayPal accounts and then demand payment for the return of the accounts.
A computer specialist by trade, the victim said he was targeted because he’d invested in a cryptocurrency startup, and that the hackers found his contact information from a list of investors they’d somehow obtained. As luck would have it, he didn’t have much of value to steal in his accounts.
The victim said he learned more about his tormentors and exactly how they’d taken over his mobile number after they invited him to an online chat to negotiate a price for the return of his accounts.
“They told me they had called a Verizon employee line [posing as a Verizon employee] and managed to get my Verizon account ID number,” said my victim source. “Once they had that, they called Verizon customer service and had them reset the password. They literally just called and pretended to be me, and were able to get my account tied to another SIM card.”
The victim said his attackers even called his mom because the mobile account was in her name. Soon after that, his phone went dead.
“The funny thing was, after I got my account back the next day, there was a voicemail from a Verizon customer service agent who said something like, ‘Hey [omitted], heard you were having trouble with your line, hope the new SIM card is working okay, give us a call if not, have a nice day.'”
RECKONING
The indictments against Hared and Ditman come amid a series of arrests, charges and sentences targeting admitted and suspected SIM swappers. Last week, Joel Ortiz — a 20-year-old college student valedictorian accused of stealing more than $5 million in cryptocurrency in a slew of SIM hijacking attacks — became the first to be convicted for the crime, accepting a plea deal for a 10-year prison term.
Many of the people being arrested and charged with SIM swapping were part of a tight circle of individuals who spent money almost as quickly as they stole it. The video below was posted to the Instagram account “O,” a username that was hijacked by Ortiz. The video shows a birthday party celebration for Xzavyer Narvarez at the Hyde Sunset club in Los Angeles. Notice the Twitter bird symbols at the bottom of each card brought out by the club’s female attendants.
Another video posted by Ortiz — to a hijacked, highly sought Instagram account “T” — shows members of this group dumping out $200 bottles of glow-in-the-dark Dom Perignon champagne onto designer watches that cost thousands of dollars each.
Also last week, 20-year-old Dawson Bakies pleaded not guilty in Manhattan Supreme Court to 52 counts of identity theft, grand larceny, and computer trespass tied to alleged SIM swapping activity. According to the New York Post, Bakies, who lives with his mom in Columbus, Ohio, allegedly called customer-service representatives posing as his victims and was able to port their phone numbers to a device he controlled.
In November 2018, authorities in New York arrested 21-year-old Manhattan resident Nicholas Truglia on suspicion of using SIM swaps to steal approximately $1 million worth of cryptocurrencies from a Silicon Valley executive. Truglia also is being sued by cryptocurrency angel investor Michael Terpin, who alleges that Truglia used a SIM swap against AT&T to steal $24 million in cryptocurrencies from him.
WHAT CAN YOU DO?
SIM swappers tend to target people with plenty of funds in the bank or in cryptocurrency exchanges, but as my victim source’s story shows, they often also SIM swap individuals who only appear to be high rollers. In the process, they may also rifle through your personal email and try to extort victims in exchange for turning over access to hijacked accounts.
There are several steps that readers can take to insulate themselves from SIM swapping attacks. First and foremost, do not re-use passwords to important accounts anywhere else. Also, take full advantage of the most robust form of multi-factor authentication available for the accounts you care about.
The web site twofactorauth.org breaks down online service providers by the types of secondary authentication offered (SMS, call, app-based one-time codes, security keys). Take a moment soon to review this important resource and harden your security posture wherever possible.
If the only two-factor authentication offered by a company you use is based on sending a one-time code via SMS or automated phone call, this is still better than relying on simply a password alone. But one-time codes generated by a mobile phone app such as Authy or Google Authenticator are more secure than SMS-based options because they are not directly vulnerable to SIM-swapping attacks. If available, physical security keys are an even better option.
Further reading:
Hanging Up on Mobile in the Name of Security
Busting SIM Swappers and SIM Swap Myths
from
https://krebsonsecurity.com/2019/02/more-alleged-sim-swappers-face-justice/
No comments:
Post a Comment