Cybercriminals are auctioning off access to customer information stolen from an online data broker behind a dizzying array of bait-and-switch Web sites that sell access to a vast range of data on U.S. consumers, including DMV and arrest records, genealogy reports, phone number lookups and people searches. In an ironic twist, the marketing empire that owns the hacked online properties appears to be run by a Canadian man who’s been sued for fraud by the U.S. Federal Trade Commission, Microsoft and Oprah Winfrey, to name a few.
Earlier this week, a cybercriminal on a Dark Web forum posted an auction notice for access to a Web-based administrative panel for an unidentified “US Search center” that he claimed holds some four million customer records, including names, email addresses, passwords and phone numbers. The starting bid price for that auction was $800.
Several screen shots shared by the seller suggested the customers in question had all purchased subscriptions to a variety of sites that aggregate and sell public records, such as dmv.us.org, carhistory.us.org, police.us.org, and criminalrecords.us.org.
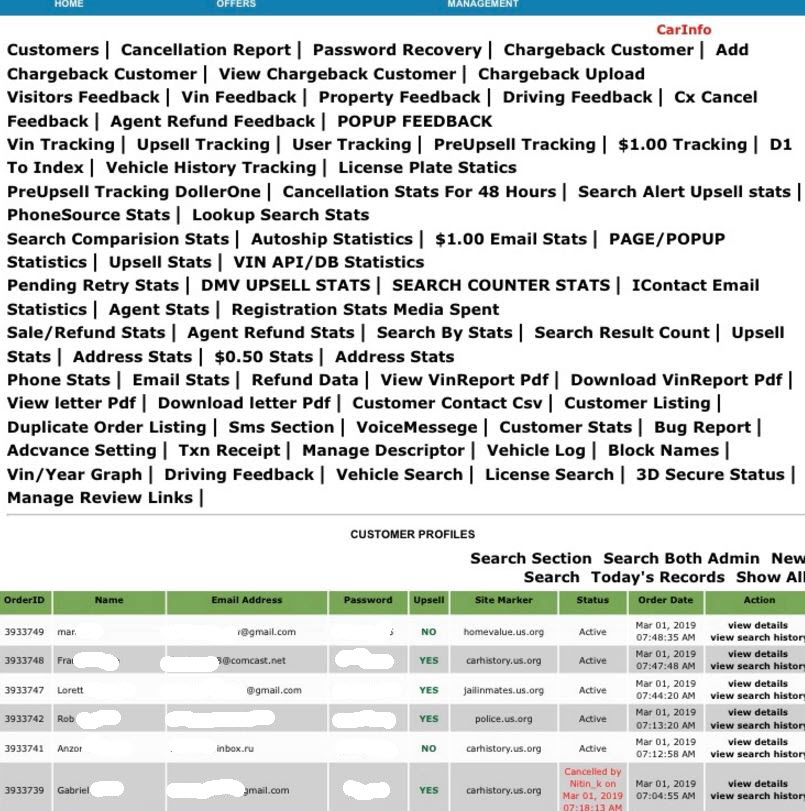
A (redacted) screen shot shared by the apparent hacker who was selling access to usernames and passwords for customers of multiple data-search Web sites.
A few hours of online sleuthing showed that these sites and dozens of others with similar names all at one time shared several toll-free phone numbers for customer support. The results returned by searching on those numbers suggests a singular reason this network of data-search Web sites changed their support numbers so frequently: They quickly became associated with online reports of fraud by angry customers.
That’s because countless people who were enticed to pay for reports generated by these services later complained that although the sites advertised access for just $1, they were soon hit with a series of much larger charges on their credit cards.
Using historic Web site registration records obtained from Domaintools.com (a former advertiser on this site), KrebsOnSecurity discovered that all of the sites linked back to two related companies — Las Vegas, Nev.-based Penguin Marketing, and Terra Marketing Group out of Alberta, Canada.
Both of these entities are owned by Jesse Willms, a man The Atlantic magazine described in an unflattering January 2014 profile as “The Dark Lord of the Internet” [not to be confused with The Dark Overlord].
Jesse Willms’ Linkedin profile.
The Atlantic pointed to a sprawling lawsuit filed by the Federal Trade Commission, which alleged that between 2007 and 2011, Willms defrauded consumers of some $467 million by enticing them to sign up for “risk free” product trials and then billing their cards recurring fees for a litany of automatically enrolled services they hadn’t noticed in the fine print.
“In just a few months, Willms’ companies could charge a consumer hundreds of dollars like this, and making the flurry of debits stop was such a convoluted process for those ensnared by one of his schemes that some customers just canceled their credit cards and opened new ones,” wrote The Atlantic’s Taylor Clark.
Willms’ various previous ventures reportedly extended far beyond selling access to public records. In fact, it’s likely everyone reading this story has at one time encountered an ad for one of his dodgy, bait-and-switch business schemes, The Atlantic noted:
“If you’ve used the Internet at all in the past six years, your cursor has probably lingered over ads for Willms’s Web sites more times than you’d suspect. His pitches generally fit in nicely with what have become the classics of the dubious-ad genre: tropes like photos of comely newscasters alongside fake headlines such as “Shocking Diet Secrets Exposed!”; too-good-to-be-true stories of a “local mom” who “earns $629/day working from home”; clusters of text links for miracle teeth whiteners and “loopholes” entitling you to government grants; and most notorious of all, eye-grabbing animations of disappearing “belly fat” coupled with a tagline promising the same results if you follow “1 weird old trick.” (A clue: the “trick” involves typing in 16 digits and an expiration date.)”
In a separate lawsuit, Microsoft accused Willms’ businesses of trafficking in massive quantities of counterfeit copies of its software. Oprah Winfrey also sued a Willms-affiliated site (oprahsdietscecrets.com) for linking her to products and services she claimed she had never endorsed.
KrebsOnSecurity reached out to multiple customers whose name, email address and cleartext passwords were exposed in the screenshot shared by the Dark Web auctioneer who apparently hacked Willms’ Web sites. All three of those who responded shared roughly the same experience: They said they’d ordered reports for specific criminal background checks from the sites on the promise of a $1 risk-free fee, never found what they were looking for, and were subsequently hit by the same merchant for credit card charges ranging from $20 to $38.
I also pinged several customer support email addresses tied to the data-broker Web sites that were hacked. I received a response from a “Mike Stef,” who described himself as a Web developer for Terra Marketing Group.
Stef said the screenshots appeared to be legitimate, and that the company would investigate the matter and alert affected customers if warranted. Stef told me he doubts the company has four million customers, and that the true number was probably closer to a half million. He also insisted that the panel in question did not have access to customer credit card data.
Nevertheless, it appears from the evidence above that Willms and several others who were named in the FTC’s 2012 stipulated final judgment (PDF) are still up to their old tricks. The FTC has not yet responded to requests for comment. Nor has Mr. Willms.
I can’t help express feeling a certain amount of schadenfreude (schadenfraud?) at the victim in this hacking case. But that amusement is tempered by the reality that the hundreds of thousands or possibly millions of people who got suckered into paying money to this company are quite likely to find themselves on the receiving end of additional phishing and fraud attacks (particularly credential stuffing) as a result of their data being auctioned off to the highest bidder.
Terra Marketing Group’s Web developer Mike Stef responded to my inquiries from an email address at the domain “tmgbox.com.” That message was instrumental in identifying the connection to Willms and Terra Marketing/Penguin. In the interests of better informing people who might wish to become future customers of this group, I am publishing the list of the domains associated with tmgbox.com and its parent entities. This list may be updated periodically as new information surfaces.
In case it is useful for others, KrebsOnSecurity is also publishing the results of several reverse WHOIS lookups for historic domains tied to email addresses of several people Mike Stef described as “senior customer support managers” of Terra Marketing, as these also include some interesting and related (albeit mostly dead) domains.
Reverse WHOIS on Peter Graver and Jesse Willms (rickholl2k9@gmail.com)
Reverse WHOIS on mike@tmgbox.com
Reverse WHOIS on Jason Oster (joster2008@gmail.com)
Public records search domains associated with Terra Marketing Group and Penguin Marketing:
memberreportaccess.com
publicrecords.us.org
dmvrecords.co
dmv.us.org
courtrecords.us.org
myfeeplan.com
police.us.org
warrantcheck.com
myinfobill.com
propertysearch.us.org
homevalue.us.org
carinfo2.com
backgroundchecks.us.org
arrestrecords.us.org
propertyrecord.com
criminalrecords.us.org
jailinmates.us.org
vehiclereportusa.com
dmvinfocheck.com
carrecordusa.com
carhistoryindex.com
autohistorychecks.com
mugshots.us.org
trafficticket.us.org
prison.us.org
reversephonelookup.us.org
deathrecords.us.org
deathrecord.com
deathcertificates.us.org
census.us.org
phonelookup.us.org
vehiclehistoryreports.us.org
vinsearchusa.org
from
https://krebsonsecurity.com/2019/03/hackers-sell-access-to-bait-and-switch-empire/
No comments:
Post a Comment