A little-known feature of many modern smartphones is their ability to duplicate video on the device’s screen so that it also shows up on a much larger display — like a TV. However, new research shows that this feature may quietly expose users to a simple and cheap new form of digital eavesdropping.
Dubbed “video jacking” by its masterminds, the attack uses custom electronics hidden inside what appears to be a USB charging station. As soon as you connect a vulnerable phone to the appropriate USB charging cord, the spy machine splits the phone’s video display and records a video of everything you tap, type or view on it as long as it’s plugged in — including PINs, passwords, account numbers, emails, texts, pictures and videos.

Some of the equipment used in the “video jacking” demonstration at the DEF CON security conference last week in Las Vegas. Source: Brian Markus.
[Click here if you’re the TL;DR type and just want to know if your phone is at risk from this attack.]
Demonstrations of this simple but effective mobile spying technique were on full display at the DEF CON security conference in Las Vegas last week. I was busy chasing a story at DEF CON unrelated to the conference this year, so I missed many people and talks that I wanted to see. But I’m glad I caught up with the team behind DEF CON’s annual and infamous “Wall of Sheep,” a public shaming exercise aimed at educating people about the dangers of sending email and other plain text online communications over open wireless networks.
Brian Markus, co-founder and chief technology officer for Aries Security, said he and fellow researchers Joseph Mlodzianowski and Robert Rowley came up with the idea for video jacking when they were brainstorming about ways to expand on their “juice jacking” experiments at DEF CON in 2011.
“Juice jacking” refers to the ability to hijack data stored data when the user unwittingly plugs his phone into a custom USB charging station filled with computers that are ready to suck down and record said data (both Android and iOS phones now ask users whether they trust the computer before allowing data transfers).
In contrast, video jacking lets the attacker record every key and finger stroke the user makes on the phone, so that the owner of the evil charging station can later replay the videos and see any numbers or keys pressed on the smart phone.
That’s because those numbers or keys will be raised briefly on the victim’s screen with each key press. Here’s an example: While the user may have enabled a special PIN that needs to be entered before the phone unlocks to the home screen, this method captures even that PIN as long as the device is vulnerable and plugged in before the phone is unlocked.
GREAT. IS MY PHONE VULNERABLE?
Markus said video jacking is not an issue for Apple iPhone users; iPhones don’t have the native HDMI-out capability via the power charging port. Most of the phones vulnerable to video jacking are Android or other HDMI-ready smartphones from Asus, Blackberry, HTC, LG, Samsung, and ZTE. This page of HDMI enabled smartphones at phonerated.com should not be considered all-inclusive. Here’s another list. When in doubt, search online for your phone’s make and model to find out if it is HDMI or MHL ready.
Video jacking is a problem for users of HDMI-ready phones mainly because it’s very difficult to tell a USB cord that merely charges the phone versus one that also taps the phone’s video-out capability. Also, there’s generally no warning on the phone to alert the user that the device’s video is being piped to another source, Markus said.
“All of those phones have an HDMI access feature that is turned on by default,” he said. “A few HDMI-ready phones will briefly flash something like ‘HDMI Connected’ whenever they’re plugged into a power connection that is also drawing on the HDMI feature, but most will display no warning at all. This worked on all the phones we tested with no prompting.”
Markus had to explain to curious DEF CON attendees who wandered near the Wall of Sheep this year exactly what would happen if they plugged their phone into his phony charging station. As you can imagine, not a ton of people volunteered but there were enough to prove a point, Markus said.
WHAT’S A FAKE CHARGING STATION?
The demonstration unit that Markus and his team showed at DEF CON (pictured above) was fairly crude. Behind a $40 monitor purchased at a local Vegas pawn shop is a simple device that takes HDMI output from a video splitter. That splitter is connected to two micro USB to HDMI cables that are cheaply available in electronics stores.
Those two cords were connected to standard USB charging cables for mobiles — including the universal micro USB to HDMI adapter (a.k.a. Mobile High Definition Link or MHL connector), and a slimport HDMI adapter. Both look very similar to standard USB charging cables. The raw video files are recorded by a simple inline recording device to a small USB storage device taped to the back of the monitor.
Markus said the entire rig (minus the TV monitor) cost about $220, and that the parts could be bought at hundreds of places online.
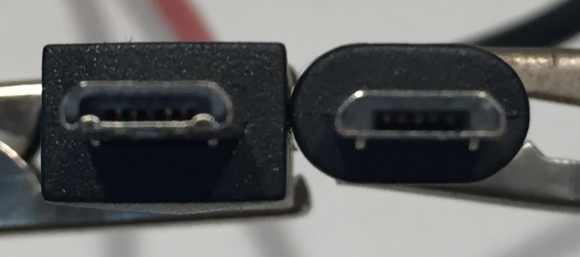
Although it may be difficult to tell the difference at this angle, the Mobile High Definition Link (MHL) USB connector on the left has a set of six extra pins that enable it to read HDMI video and whatever is being viewed on the user’s screen. Both cords will charge the same phone.
SHOULD YOU CARE?
My take on video jacking? It’s an interesting and very real threat — particularly if you own an HDMI ready phone and are in the habit of connecting it to any old USB port. Do I consider it likely that any of us will have to worry about this in real life? The answer may have a lot to do with what line of work you’re in and how paranoid you are, but it doesn’t strike me as very likely that most mere mortals would have reason to worry about video jacking.
On the other hand, it would be a fairly cheap and reasonably effective (if random) way to gather secrets from a group of otherwise unsuspecting people in a specific location, such as a hotel, airport, pub, or even a workplace.
An evil mobile charging station would be far more powerful when paired with a camera (hidden or not) trained on the charger. Imagine how much data one could hoover up with a fake charging station used to gather intellectual property or trade secrets from, say….attendees of a niche trade show or convention.
Now that I think about it, since access to electric power is not a constraint with these fake charging stations, there’s no reason it couldn’t just beam all of its video wirelessly. That way, the people who planted the spying equipment could retrieve or record the victim videos in real time and never have to return to the scene of the crime to collect any of it. Okay, I’ll stop now.
What can vulnerable users do to protect themselves from video jacking?
Hopefully, your phone came with a 2-prong charging cord that plugs straight into a standard wall jack. If not, look into using a USB phone charger adapter that has a regular AC/DC power plug on one end and a female USB port on the other (just make sure you don’t buy this keystroke logger disguised as a USB phone charger). Carry an extra charging dock for your mobile device when you travel.
What should mobile device makers do to minimize the threat from video jacking?
“The problem here is that device manufacturers continue to add features and not give us prompting,” Markus said. “With this feature, it automatically connects no matter what. HDMI-out should be off by default, and if turned on it should require prompting the user.”
from
http://redirect.viglink.com?u=http%3A%2F%2Fkrebsonsecurity.com%2F2016%2F08%2Froad-warriors-beware-of-video-jacking%2F&key=ddaed8f51db7bb1330a6f6de768a69b8
No comments:
Post a Comment