In April 2016, security firm Trend Micro published a damning report about a Web hosting provider referred to only as a “cyber-attack facilitator in the Netherlands.” If the Trend analysis lacked any real punch that might have been because — shortly after the report was published — names were redacted so that it was no longer immediately clear who the bad hosting provider was. This post aims to shine a bit more light on the individuals apparently behind this mysterious rogue hosting firm — a company called HostSailor[dot]com.
The Trend report observes that the unnamed, Netherlands-based virtual private sever (VPS) hosting provider appears to have few legitimate customers, and that the amount of abuse emanating from it “is so staggering that this company will remain on our watchlist in the next few months.”
What exactly is the awfulness spewing from the company that Trend takes great pains not to name as HostSailor.com? For starters, according to Trend’s data (PDF) HostSailor has long been a home for attacks tied to a Russian cyber espionage campaign dubbed “Pawn Storm.” From the report:
“Pawn Storm seems to feel quite at home. They used the VPS hosting company for at least 80 attacks since May 2015. Their attacks utilized C&C servers, exploit sites, spear-phishing campaigns, free Webmail phishing sites targeting high profile users, and very specific credential phishing sites against Government agencies of countries like Bulgaria, Greece, Malaysia, Montenegro, Poland, Qatar, Romania, Saudi Arabia, Turkey, Ukraine, and United Arab Emirates. Pawn Storm also uses the VPS provider in the Netherlands for domestic espionage in Russia regularly.”
“Apart from Pawn Storm, a less sophisticated group of threat actors called DustySky (PDF link added) is using the VPS provider. These actors target Israel, companies who do business in Israel, Egypt and some other Middle Eastern governments.”
WHO IS HOSTSAILOR?
Trend’s report on HostSailor points to a LinkedIn profile for an Alexander Freeman at HostSailor who lists his location as Dubai. HostSailor’s Web site says the company has servers in The Netherlands and in Romania, and that it is based in Dubai. The company first came online in early 2013.
Ron Guilmette, an anti-spam researcher who tipped me off to the Trend report and whose research has been featured several times on this blog, reached out to Freeman via email. Guilmette later posted at the Ripe.net mailing list the vitriolic and threatening response he said he received in reply.
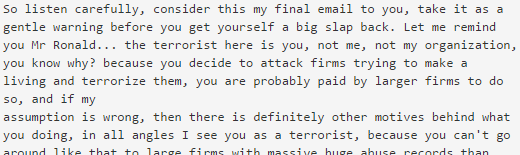
A snippet from the response that Guilmette said he received from a HostSailor employee named Alexander Freeman.
Perhaps Mr. Freeman’s ire was previously leveled at Trend Micro, which could explain their redaction of the name “HostSailor” from its report. A spokesperson for Trend Micro declined to explain why the company redacted its own report post-publication, saying only that “at the time of publication, we were following our standard disclosure protocol.”
In any case, I began to suspect that “Alexander Freeman” was just a pseudonym (Trend noted this suspicion in its report as well). In combing through the historic WHOIS registration records for the domain hostsailor.com, I noticed that the domain name changed hands sometime in late 2012. Sure enough, a simple Google search popped up this thread at Webhostingtalk.com back in Dec. 2012, which was started by a Jordan Peterson who says he’s looking to sell hostsailor.com.
Contacted by KrebsOnSecurity, Mr. Peterson said the person who responded about purchasing the domain was named Ali Al-Attiyah, and that this individual used the following email addresses:
ali.alattiyah@yahoo.com
ali.alattiyah@mail.com
hostsailor@hush.com
“I remember Ali telling me he didn’t have a paypal so a friend sent me the money for the domain, I looked up the paypal info for you and [Ali’s friend’s] name is Khalid Cook, masrawyz@yahoo.com,” Peterson told me. “The legal information for the domain transfer was given as:
152-160 City Road
London ec1v 2nx
UK”
That street address corresponds to a business named “yourvirtualofficelondon.co.uk,” which offers call answering services for companies that wish to list a prestigious London address without actually having a physical presence there.
Ali Al-Attiyah is listed as the official registrant of hostsailor.com and several other very similar domains. More interesting, however, is that email address given for Mr. Khalid Cook: masrawyz@yahoo.com. According to a “reverse WHOIS” search ordered from DomainTools.com, that Yahoo email address was used in the original registration records for exactly one domain: santrex.net.
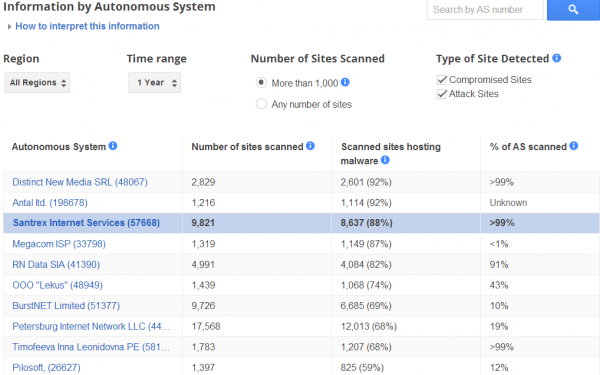
Santrex (better known on Webhostingtalk.com as “Scamtrex“) was an extremely dodgy “bulletproof hosting” company — essentially a mini-ISP that specializes in offering services that are largely immune from takedown requests and pressure from Western law enforcement agencies. At the time, Google’s Safebrowsing database warned that almost 90 percent of the sites on Santrex’s network were attempting to foist malicious software on visitors or were hosting malware used in online attacks.
Santrex was forced out of business in early 2013, after the company’s core servers were massively hacked and the PayPal and credit card accounts it used to accept payments from customers were reportedly seized by unknown parties. In its final days as a hosting provider, Santrex’s main voice on Webhostingtalk.com — a user named “khalouda” — posted many rants that eerily echo the invective leveled at Guilmette by HostSailor’s Mr. Freeman.
WHO IS KHALID COOK?
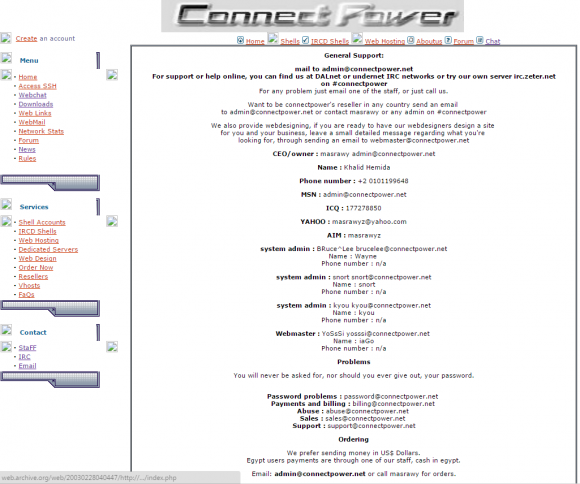
I began to suspect that Khalid Cook may also be a pseudonym. A few minutes of digging online unearthed this February 2013 Santrex profile at gidforums[dot]net, which states that Santrex first appeared in 2001 as a hosting company called connectpower[dot]net.
Alas, the original WHOIS registration records for connectpower[dot]net indicate that it was registered November 2001 to a Khalid Hemida, an individual who gave a physical address in Egypt and the email address botland@masrawy.com. This archive.org cache of connectpower[dot]net’s “Staff” page seems to confirm the organization’s presence in Egypt, saying ConnectPower customers living in Egypt can pay through one of the staff members, in cash. This page also reveals Hemida’s ICQ number.
A Google search on Khalid Hemida turns up at least two different connectpower[dot]net business listings which include the email address khalidhemida@hotmail.com, and which claim the Web site “botland.org.”
That Hotmail address appears to have been used to register a Facebook account for a user from Doha, Qatar who registered under the name Khalid Hemida but who is now using the name “Karam Khalid.” The account’s profile picture apparently was lifted from an issue of BusinessWeek, according to the image search service Tineye.com. A different Khalid Hemida account on Facebook belongs to an older individual who says he’s from Egypt and that his current town is Dubai.
But what of that “botland” reference — both the botland@masrawy.com address claimed by Hemida and the domain botland[dot]org? This cached page of botland[dot]org recorded by the Internet Archive in June 2011 references “an automated BotLending Channel,” run by at least four main users from Romania.
Botland was a channel on Undernet, a vast sea of text-based communities called Internet Relay Chat (IRC) networks. Botland was a place where people could download special bots designed to manage users and preserve order on an IRC server, but mainly to guard the channel from being hijacked by other users or bots. The reason I mention it is that Undernet in 2001 would have been the perfect place to meet new customers seeking dodgy Web hosting businesses.
To bring this full circle back to the Trend Report: I should note that if HostSailor is being truthful about where the company is incorporated — in Dubai — then it has long been facilitating the aforementioned Pawn Storm cyber espionage attacks against its own host country. For that reason, I imagine some government authorities within the United Arab Emirates might be interested in looking more closely into HostSailor and its operations.
For the record, I requested comment from HostSailor and from the various addresses listed in this story for Messrs. Freeman, Cook and Hemida. I’ll update this story in the event that any of these pings generate a reply.
from
http://redirect.viglink.com?u=http%3A%2F%2Fkrebsonsecurity.com%2F2016%2F08%2Fthe-reincarnation-of-a-bulletproof-hoster%2F&key=ddaed8f51db7bb1330a6f6de768a69b8
No comments:
Post a Comment