A decade ago, if a desktop computer got infected with malware the chief symptom probably was an intrusive browser toolbar of some kind. Five years ago you were more likely to whacked by a banking trojan that stole all your passwords and credit card numbers. These days if your mobile or desktop computer is infected what gets installed is likely to be “ransomware” — malicious software that locks your most prized documents, songs and pictures with strong encryption and then requires you to pay for a key to unlock the files.
Here’s some basic advice about where to go, what to do — and what not to do — when you or someone you know gets hit with ransomware.
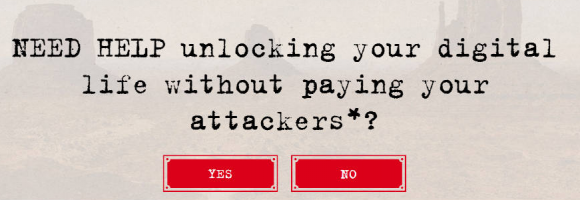
Image: nomoreransom.org
First off — breathe deep and try not to panic. And don’t pay the ransom.
True, this may be easier said than done: In many cases the ransom note that hijacks the victim’s screen is accompanied by a digital clock ominously ticking down the minutes and seconds from 72 hours. When the timer expires, the ransom demand usually goes up or even doubles. Continue to ignore the demands and your files will be gone, kaput, nil, nyet, zilch, done forever, warns the extortion message.
See, the key objective of ransomware is a psychological one — to instill fear, uncertainty and dread in the victim — and to sow the conclusion in the victim’s mind that any solution for restoring full access to all his files involves paying up. Indeed, paying the ransom is often the easiest, fastest and most complete way of reversing a security mistake, such as failing to patch, opening a random emailed document e.g., or clicking a link that showed up unbidden in instant message. Some of the more advanced and professional ransomware operations have included helpful 24/7 web-based tech support.
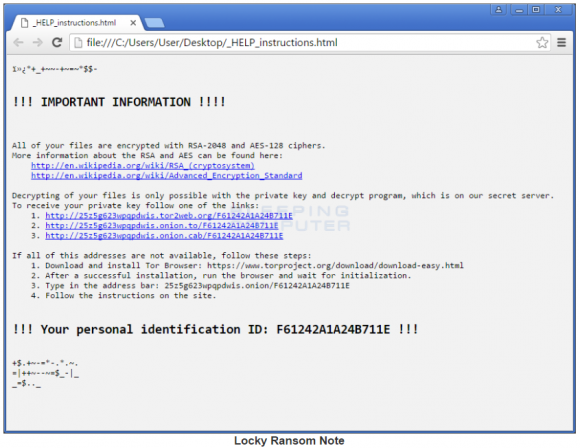
The ransom note from a recent version of the “Locky” ransomware variant. Image: Bleepingcomputer.com.
Paying up is certainly not the cheapest option. The average ransom demanded is approximately $722, according to an analysis published in September by Trend Micro. Interestingly, Trend found the majority of organizations that get infected by ransomware end up paying the ransom. They also found three-quarters of companies which had not suffered a ransomware infection reported they would not pay up when presented with a data ransom demand. Clearly, people tend to see things differently when they’re the ones in the hot seat.
And for those not yet quite confident in the ways of Bitcoin (i.e. most victims), paying up means a crash course in acquiring the virtual currency known as Bitcoin. Some ransomware attackers are friendlier than others in helping victims wade through the process of setting up an account to handle Bitcoin, getting it funded, and figuring out how to pay other people with it. Others just let you figure it all out. The entire ordeal is a trial by fire for sure, but it can also be a very expensive, humbling and aggravating experience.
In the end the extortionist may bargain with you if they’re in a good mood, or if you have a great sob story. But they still want you to know that your choice is a binary one: Pay up, or kiss your sweet files goodbye forever.
This scenario reminds me of the classic short play/silent movie about the villainous landlord and the poor young lady who can’t pay the rent. I imagine the modern version of this play might go something like…
 Villain: You MUST pay the ransom!
Villain: You MUST pay the ransom!
Victim: I CAN’T pay the ransom!
Villain: You MUST pay the ransom!
Victim: I CAN’T pay the ransom!
Hero: I’ll pay the ransom!
Victim: Oh! My hero!
Villain: Curses! Foiled again!
Okay, nobody’s going to pay the ransomware demand for you (that’s only in Hollywood!). But just like the hero in the silent movie, there are quite a few people out there who are in fact working hard to help victims avoid paying the ransom (AND get their files back to boot).
Assuming you don’t have a recent backup you can restore, fear not: With at least some strains of ransomware, the good guys have already worked out a way to break or sidestep the encryption, and they’ve posted the keys needed to unlock these malware variants free of charge online.
But is the strain that hit your device one that experts already know how to crack?
WHERE TO GO?
The first place victims should look to find out is nomoreransom.org, a site backed by security firms and cybersecurity organizations in 22 countries. Since its launch on July 25, 2016, nomoreransom.org estimates that it has been able to save 6,000 victims of ransomware more than $2 million USD to date. Last week the group announced the site is now available in Dutch, French, Italian, Portuguese and Russian.
Visit the Crypto Sheriff page at nomoreransom.org, upload one of the files encrypted by the ransomware, and the site will let you know if there is a solution available to unlock all of your files for free.
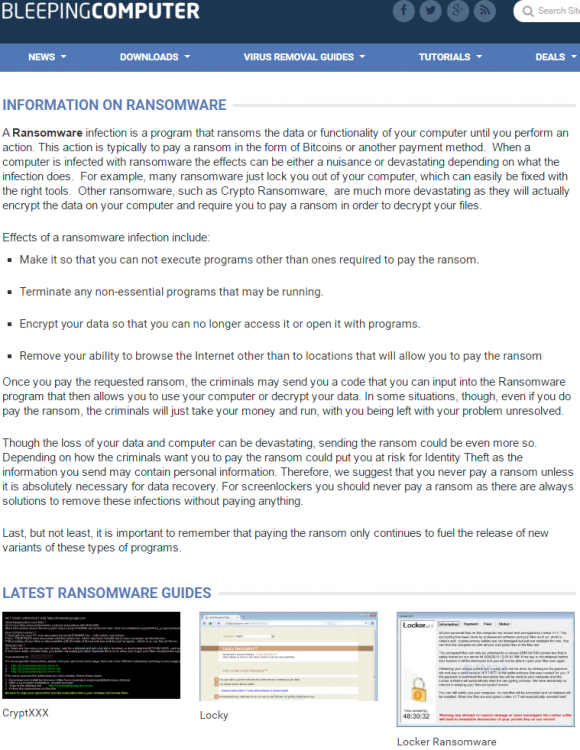
Another destination that may be useful for ransomware victims is bleepingcomputer.com, which has an excellent Ransomware Help and Tech Support section that is quite useful and may save you a great deal of time and money. But please don’t just create an account here and cry for help. Your best bet is to read the “pinned” notes at the top of that section and follow the instructions carefully.
Chances are, whoever responds to your request will want you to have run a few tools to help identify which strain of ransomware hit your system before agreeing to help. So please be patient and be kind, and remember that if someone decides to help you here they are likely doing so out of their own time and energy.
HOW NOT TO BE THE NEXT RANSOMWARE VICTIM
Regularly backup your data, and make sure the backups are not connected to the computers and networks they are backing up. Most ransomware variants can encrypt files on any attached drives or network files that are also accessible to the host machine (including cloud hosting and cloud-based backups if those passwords are stored on the machine). Bleepingcomputer’s Lawrence Abrams just published this a nice primer called How to Protect and Harden a Computer Against Ransomware.
Many companies are now selling products that claim to block ransomware attacks. Those claims are beyond the scope of this article, but don’t be lulled into thinking these products will always protect you.
Even products that could somehow block all ransomware attacks can’t prevent the biggest reason that ransomware attacks succeed: They trick victims into taking an action that inadvertently undermines the security of their device — be it a smart phone, tablet or desktop computer.
This usually involves clicking a link or downloading and opening a file that arrives in an email or instant message. In either case, it is an action that opens the door to the attacker to download and install malware.
Remember my Three Rules of Online Security:

…For Online Safety.
1: If you didn’t go looking for it, don’t install it.
2: If you installed it, update it.
3: If you no longer need it (or, if it’s become too big of a security risk) get rid of it.
These rules apply no matter what device you use to get online, but I’ll add a few recommendations here that are more device-specific. For desktop users, some of the biggest risks come from insecure browser plugins, as well as malicious Microsoft Office documents and “macros” sent via email and disguised as invoices or other seemingly important, time-sensitive documents.
Microsoft has macros turned off by default in most modern Office versions because they allow attackers to take advantage of resources on the target’s computer that could result in running code on the system. So understand that responding affirmatively to an “Enable Macros?” prompt in an Office document you received externally and were not expecting is extremely risky behavior.
Enterprises can use a variety of group policy changes to harden their defenses against ransomware attacks, such as this one which blocks macros from opening and automatically running in Office programs on Windows 10. Other ransomware-specific group policy guides are here, here and here (happy to add more “here’s” here if they are worthy, let me know).
Also, get rid of or hobble notoriously insecure, oft-targeted browser plugins that require frequent security updates — like Java and Flash. If you’re not good about updating these programs frequently, you may fall victim to an exploit kit that delivers ransomware. Exploit kits are malicious programs made to be stitched into hacked or malicious Web sites. People who visit these sites or who are redirected to them and who are browsing the Web with an outdated version of Flash or Java can have malware automatically and quietly installed.
Mobile users in general need to spend just a tiny fraction more time discerning the origin and reputation of the applications they wish to install, as mobile ransomware variants tend to mimic or even piggyback on popular games and applications found in app stores and other places. Don’t just download the first app that matches your search. And always download from the original source whenever possible to ensure you’re not getting a copycat, counterfeit or malicious version of the game or application that you’re seeking.
For more tips on how not to become the next ransomware victim, check out the bottom half of the FBI’s most recent advisory on the topic.
from
https://krebsonsecurity.com/2016/12/before-you-pay-that-ransomware-demand/
No comments:
Post a Comment