Addressing distributed denial-of-service (DDoS) attacks designed to knock Web services offline and security concerns introduced by the so-called “Internet of Things” (IoT) should be top cybersecurity priorities for the 45th President of the United States, according to a newly released blue-ribbon report commissioned by President Obama.
 “The private sector and the Administration should collaborate on a roadmap for improving the security of digital networks, in particular by achieving robustness against denial-of-service, spoofing, and other attacks on users and the nation’s network infrastructure,” reads the first and foremost cybersecurity recommendation for President-elect Donald Trump. “The urgency of the situation demands that the next Administration move forward promptly on our recommendations, working closely with Congress and the private sector.”
“The private sector and the Administration should collaborate on a roadmap for improving the security of digital networks, in particular by achieving robustness against denial-of-service, spoofing, and other attacks on users and the nation’s network infrastructure,” reads the first and foremost cybersecurity recommendation for President-elect Donald Trump. “The urgency of the situation demands that the next Administration move forward promptly on our recommendations, working closely with Congress and the private sector.”
The 12-person, non-partisan commission produced a 90-page report (PDF) and recommended as their very first action item that the incoming President “should direct senior federal executives to launch a private–public initiative, including provisions to undertake, monitor, track, and report on measurable progress in enabling agile, coordinated responses and mitigation of attacks on the users and the nation’s network infrastructure.”
The panel said this effort should build on previous initiatives, such as a 2011 program by the U.S. Department of Commerce called the Industry Botnet Group.
“Specifically, this effort would identify the actions that can be taken by organizations responsible for the Internet and communications ecosystem to define, identify, report, reduce, and respond to attacks on users and the nation’s network infrastructure,” the report urged. “This initiative should include regular reporting on the actions that these organizations are already taking and any changes in technology, law, regulation, policy, financial reimbursement, or other incentives that may be necessary to support further action—while ensuring that no participating entity obstructs lawful content, applications, services, or nonharmful devices, subject to reasonable network management.”
The report spans some six major imperatives, including 16 recommendations and 63 associated action items. The second major imperative focuses on IoT security concerns, and urges the federal government and private industry to embark upon a number of initiatives to “rapidly and purposefully to improve the security of the Internet of Things.”
“The Department of Justice should lead an interagency study with the Departments of Commerce and Homeland Security and work with the Federal Trade Commission, the Consumer Product Safety Commission, and interested private sector parties to assess the current state of the law with regard to liability for harm caused by faulty IoT devices and provide recommendations within 180 days,” the panel recommended. “To the extent that the law does not provide appropriate incentives for companies to design security into their products, and does not offer protections for those that do, the President should draw on these recommendations to present Congress with a legislative proposal to address identified gaps, as well as explore actions that could be accomplished through executive order.”
Meanwhile, Morning Consult reports that U.S. Federal Communications Commission Chairman Tom Wheeler has laid out an unexpected roadmap through which the agency could regulate the security of IoT devices. The proposed certification process was laid out in a response to a letter sent by Sen. Mark Warner (D-Va.) shortly after the IoT-based attacks in October that targeted Internet infrastructure company Dyn and knocked offline a number of the Web’s top destinations for the better part of a day.
Morning Consult’s Brendan Bordelon notes that while Wheeler is set to step down as chairman on Jan. 20, “the new framework could be used to support legislation enhancing the FCC’s ability to regulate IoT devices.”
ANALYSIS
It’s nice that this presidential commission placed a special emphasis on IoT and denial-of-service attacks, as these two threats alone are clear and present dangers to the stability of e-commerce and free expression online. However, this report overall reads very much like other blue-ribbon commission reports of years past: The recommendations eschew new requirements in favor of the usual calls for best practices, voluntary guidelines, increasing industry-government information sharing, public/private partnerships, and public awareness campaigns.
One recommendation I would like to have seen in this report is a call for federal legislation that requires U.S.-based hosting providers to block spoofed traffic from leaving their networks.
As I noted in a November 2015 story, The Lingering Mess from Default Insecurity, one major contributor to the massive spike in denial-of-service attacks over the past few years is that far too many ISPs and hosting providers allow traffic to leave their networks that did not originate there. Using well-known attack techniques known as traffic amplification and reflection, an attacker can “reflect” his traffic from one or more third-party machines toward the intended target.
In this type of assault, the attacker sends a message to a third party, while spoofing the Internet address of the victim. When the third party replies to the message, the reply is sent to the victim — and the reply is much larger than the original message, thereby amplifying the size of the attack. According to the latest DDoS report from Akamai, more than half of all denial-of-service attacks in the third quarter of 2016 involved reflection and spoofing.
One basic step that many ISPs and hosting providers can but apparently are not taking to blunt these spoofing attacks involves a network security standard that was developed and released more than a dozen years ago. Known as BCP38, its use prevents abusable resources on an ISP’s network from being leveraged in denial-of-service. BCP38 is designed to filter such spoofed traffic, so that the reflected traffic from the third party never even traverses the network of an ISP that’s adopted the anti-spoofing measures.
However, there are non-trivial economic reasons that many ISPs fail to adopt this best practice. This blog post from the Internet Society does a good job of explaining why many ISPs decide not to implement BCP38. Ultimately, it comes down to cost and to a fear that adoption of this best practice will increase costs and prompt some customers to seek out providers that do not enforce this requirement. In some cases, U.S.-based hosting providers that allow spoofing/reflection have been sought out and recommended among miscreants involved in selling DDoS-for-hire services.
In its Q3 2016 State of the Internet report, Akamai notes that while Chinese ISPs occupy the top two sources of spoofed traffic, several large U.S.-based providers make a showing here as well:
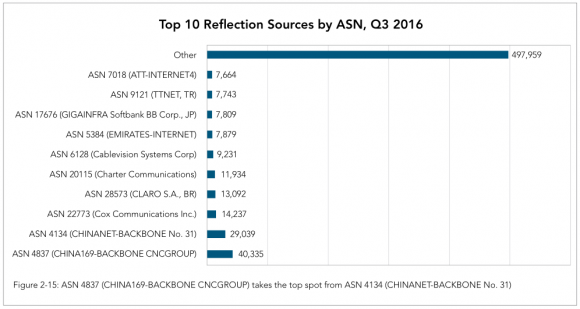
Image: Akamai.
It is true that requiring U.S. hosting providers to block spoofing would not solve the spoofing problem globally. But I believe it’s high time that the United States led by example in this arena, if only because we probably have the most to lose by continued inaction. According to Akamai, more than 21 percent of all denial-of-service attacks originate from the United States. And that number has increased from 17 percent a year ago, Akamai found. What’s more, the U.S. is the most frequent target of these attacks, according to DDoS stats released this year by Arbor Networks.
from
https://krebsonsecurity.com/2016/12/ddos-iot-top-cybersecurity-priorities-for-45th-president/
No comments:
Post a Comment