The New York Times this week published a fascinating story about a young programmer in Ukraine who’d turned himself in to the local police. The Times says the man did so after one of his software tools was identified by the U.S. government as part of the arsenal used by Russian hackers suspected of hacking into the Democratic National Committee (DNC) last year. It’s a good read, as long as you can ignore that the premise of the piece is completely wrong.
The story, “In Ukraine, a Malware Expert Who Could Blow the Whistle on Russian Hacking,” details the plight of a hacker in Kiev better known as “Profexer,” who has reportedly agreed to be a witness for the FBI. From the story:
“Profexer’s posts, already accessible to only a small band of fellow hackers and cybercriminals looking for software tips, blinked out in January — just days after American intelligence agencies publicly identified a program he had written as one tool used in Russian hacking in the United States. American intelligence agencies have determined Russian hackers were behind the electronic break-in of the Democratic National Committee.”
The Times’ reasoning for focusing on the travails of Mr. Profexer comes from the “GRIZZLYSTEPPE” report, a collection of technical indicators or attack “signatures” published in December 2016 by the U.S. government that companies can use to determine whether their networks may be compromised by a number of different Russian cybercrime groups.
The only trouble is nothing in the GRIZZLYSTEPPE report said which of those technical indicators were found in the DNC hack. In fact, Prefexer’s “P.A.S. Web shell” tool — a program designed to insert a digital backdoor that lets attackers control a hacked Web site remotely — was specifically not among the hacking tools found in the DNC break-in.
![The P.A.S. Web shell, as previously offered for free on the now-defunct site profexer[dot]name.](http://krebsonsecurity.com/wp-content/uploads/2017/08/pas30.png)
The P.A.S. Web shell, as previously offered for free on the now-defunct site profexer[dot]name.
Robert M. Lee is founder of the industrial cybersecurity firm Dragos, Inc. and an expert on the challenges associated with attribution in cybercrime. In a post on his personal blog, Lee challenged The Times on its conclusions.
“The GRIZZLYSTEPPE report has nothing to do with the DNC breach though and was a collection of technical indicators the government compiled from multiple agencies all working different Russian related threat groups,” Lee wrote.
“The threat group that compromised the DNC was Russian but not all Russian groups broke into the DNC,” he continued. “The GRIZZLYSTEPPE report was also highly criticized for its lack of accuracy and lack of a clear message and purpose. I covered it here on my blog but that was also picked up by numerous journalists and covered elsewhere [link added]. In other words, there’s no excuse for not knowing how widely criticized the GRIZZLYSTEPPE report was before citing it as good evidence in a NYT piece.”
Perhaps in response to Lee’s blog post, The Times issued a correction to the story, re-writing the above-quoted and indented paragraph to read:
“It is the first known instance of a living witness emerging from the arid mass of technical detail that has so far shaped the investigation into the election hacking and the heated debate it has stirred. The Ukrainian police declined to divulge the man’s name or other details, other than that he is living in Ukraine and has not been arrested.”
[Side note: Profexer may well have been doxed by this publication just weeks after the GRIZZLYSTEPPE report was released.]
This would not be the first time the GRIZZLYSTEPPE report provided fodder for some too-hasty hacking conclusions by a major newspaper. On December 31 2016, The Washington Post published a breathless story reporting that an electric utility in Vermont had been compromised by Russian hackers who had penetrated the U.S. electric grid.
The Post cited unnamed “U.S. officials” saying the Vermont utility had found a threat signature from the GRIZZLYSTEPPE report inside its networks. Not long after the story ran, the utility in question said it detected the malware signature in a single laptop that was not connected to the grid, and the Post was forced to significantly walk back its story.
Matt Tait, a senior fellow at the Robert Strauss Center for International Security and Law at UT Austin, said indicators of compromise or IOCs like those listed in the GRIZZLYSTEPPE report have limited value in attributing who may be responsible for an online attack.
“It’s a classic problem that these IOCs indicate you may be compromised, but they’re not very good for attribution,” Tait said. “The Grizzly Steppe report is a massive file of signatures, and loads of people have run those, found various things on their network, and then assumed it’s all related to the DNC hack. But there’s absolutely no tie between the DNC hack that in any way involved this P.A.S. Web shell.”
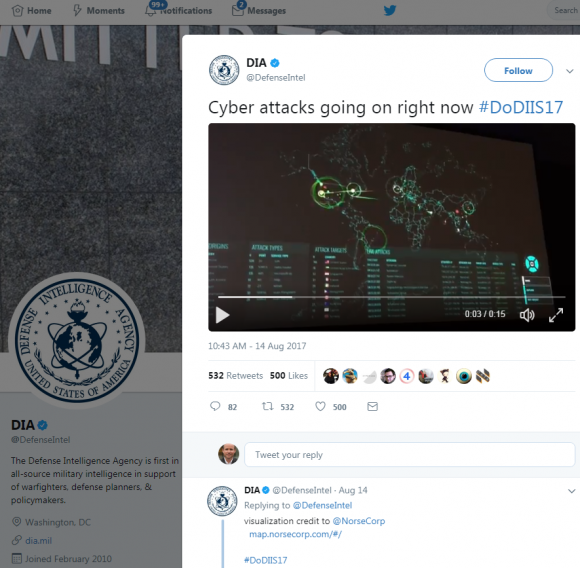
If it’s not always clear how seriously to take conclusions from Uncle Sam about the sources of cybercrime, it certainly doesn’t help when intelligence agencies are still relying on discredited sources of information about the sources of cyberattacks. As Mr. Lee observed at the top of his blog post, the Twitter account for the U.S. Defense Intelligence Agency tweeted on Aug. 14, 2017: “Cyber attacks going on right now #DoDIIS17”.
The DIA tweet included a brief video of the global threat map produced by Norse Corp., a company whose lovely but otherwise misguided efforts at cyber attack attribution have been repeatedly denounced by Lee and other cybersecurity experts. For more on how Norse self-destructed from the inside, see my Jan. 2016 story, Sources: Security Firm Norse Corp. Imploding.
One final note: Wired.com has a lengthy but tremendous new story worth reading called A Guide to Russia’s High Tech Tool Box for Subverting US Democracy. It makes a convincing case that the real, long-term goal of Russian state-sponsored hacking activity is to sow public and popular distrust in the democratic process and to weaken democratic institutions inside countries that support the North Atlantic Treaty Organization (NATO).
from
https://krebsonsecurity.com/2017/08/blowing-the-whistle-on-bad-attribution/
No comments:
Post a Comment