More online services than ever now offer two-step authentication — requiring customers to complete a login using their phone or other mobile device after supplying a username and password. But with so many services relying on your mobile for that second factor, there has never been more riding on the security of your mobile account. Below are some tips to ensure your mobile device (or, more specifically, your mobile carrier) isn’t the weakest link in your security chain.
For reasons explored more in The Value of a Hacked Email Account, many people become so preoccupied with securing online access to their financial accounts that they overlook or forget the fact that all of those precautions may be moot if hackers can access your email inbox. From that 2013 piece:
“Sign up with any service online, and it will almost certainly require you to supply an email address. In nearly all cases, the person who is in control of that address can reset the password of any associated services or accounts –merely by requesting a password reset email.”
Many webmail providers now encourage users to take advantage of two-step (a.k.a. “two factor”) authentication methods in addition to passwords for securing access to email. This usually involves the user adding a mobile phone number to their account that gets sent a one-time code that needs to be entered after supplying the account password. The idea here is that even if thieves somehow manage to phish or otherwise glean your account password, they still need access to your phone to discover the one-time code.
Depending on how you’ve set up two-step authentication, however, this may be far from airtight security. What’s more, not all two-step authentication methods are equally secure. Probably the most common form of secondary authentication — a one-time code sent to your mobile device via SMS/text message — is also the least secure.
That’s because thieves who manage to phish or otherwise filch your password can then simply ring your mobile provider pretending to be you, claiming that your phone is lost and that you need to activate a new phone and corresponding new SIM card. Or, they convince a gullible or inexperienced customer support rep to temporarily forward all of your calls and texts to a different number (this happened to me in 2013).
A harrowing story in The New York Times last week showcased several such hacks against Bitcoin enthusiasts, but in truth these types of social engineering attacks have been going on for years.
True, not everyone will attract the kind of interest from cybercrooks as someone holding large amounts of a non-repudiable virtual currency. But it’s still a good idea to take a few minutes and check whether some of the services you use that offer two-step authentication might offer an app-based method — such as Google Authenticator or Authy — as opposed to a text-based method.
By the way, I’m not the only one bugging people to move away from texting for codes: The National Institute of Standards and Technology (NIST) recently issued new proposed digital authentication guidelines urging organizations to favor other forms of two-factor — such as time-base one-time passwords generated by mobile apps — over text messaging.
Fortunately, some of the more popular online services offer multiple options for two-step authentication, although many of those that offer alternatives to texting one-time codes still steer users toward this option. I took stock of my own exposure to text-based two-step authentication and found three services I rely upon daily for my work still had the SMS option selected when a more secure app-based option was available.
Take a moment to review the authentication options available for the services you use on a regular basis. To do this, head on over to twofactorauth.org. A simple search for “Facebook,” for example, shows that the social networking site offers secondary authentication options via SMS, hardware token (such as a physical USB security key) and software token (Google Authenticator, e.g.).
In the case of Facebook, if you previously received one-time tokens via SMS, you may have to temporarily disable two-step authentication via text message before enabling the security key and software token approaches.
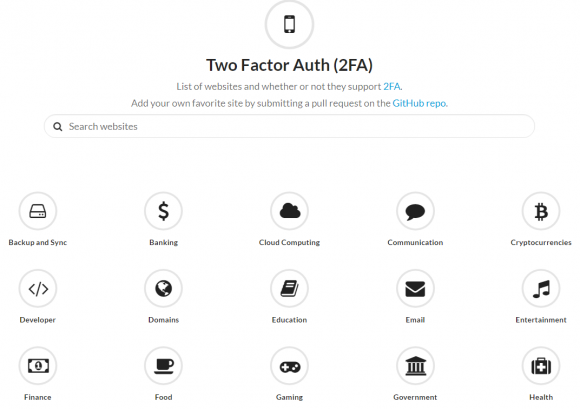
Lots of companies now offer multiple options for two-step authentication that go beyond SMS. Image: twofactorauth.org
Also, some people (present company included) need extra security and may be willing to put up with additional minor inconveniences in exchange for added peace of mind that thieves aren’t going to just waltz in and steal everything. This is particularly true for people with serious assets tied up in online sites and services that may not offer more robust authentication options.
This piece over at Techcrunch last week tells the story of another Bitcoin enthusiast who took some pretty extreme measures after someone tricked his mobile provider into switching his account to a new phone. Like requesting that the provider lock your phone’s SIM card to your device and prevent the phone from being used with another SIM card (the downside of this is if you really do lose your phone it could be much more complicated with this option turned on).
The story also recommends calling your telecommunications provider and asking them to set a passcode or PIN on your account that needs to be supplied before a customer service representative will discuss the account details.
“Make sure it applies to ALL account changes,” the Techcrunch pieces advises. “Make sure it applies to all numbers on the account. Ask them what happens if you forget the passcode. Ask them what happens if you lose that too.”
I should note that just because SMS is less secure than other forms of two-step authentication, that should not disqualify it as a worthwhile security step when more secure alternatives are unavailable. Any form of two-factor authentication is better than relying solely on usernames and passwords.
Some online services allow people to receive one-time codes via an automated phonecall. I hope it goes without saying this, but this method also is vulnerable to an attacker tricking a customer support person at your mobile provider into doing something they shouldn’t. Read the penultimate update to this 2012 blog post about how the CEO of Cloudflare had his account hacked after someone social engineered an AT&T representative into forwarding his second factor by automated phone call to a number the attackers controlled.
Finally, be judicious about what you install on your mobile device, and spend a few minutes researching the reputation and longevity of any app you wish to install before you install it. Also, pay close attention the permissions being requested by apps that you install: A mobile device compromised by mobile malware may not be the most reliable or secure second factor.
from
https://krebsonsecurity.com/2017/08/is-your-mobile-carrier-your-weakest-link/
No comments:
Post a Comment