Dec. 18 marked the fourth anniversary of this site breaking the news about a breach at Target involving some 40 million customer credit and debit cards. It has been fascinating in the years since that epic intrusion to see how organized cyber thieves have shifted from targeting big box retailers to hacking a broad swath of small to mid-sized merchants.
In many ways, not much has changed: The biggest underground shops that sell stolen cards still index most of their cards by ZIP code. Only, the ZIP code corresponds not to the legitimate cardholder’s billing address but to the address of the hacked store at which the card in question was physically swiped (the reason for this is that buyers of these cards tend to prefer cards used by people who live in their geographic area, as the subsequent fraudulent use of those cards tends to set off fewer alarm bells at the issuing bank).
Last week I was researching a story published here this week on how a steep increase in transaction fees associated with Bitcoin is causing many carding shops to recommend alternate virtual currencies like Litecoin. And I noticed that popular carding store Joker’s Stash had just posted a new batch of cards dubbed “Dynamittte,” which boasted some 7 million cards advertised as “100 percent” valid — meaning the cards were so fresh that even the major credit card issuers probably didn’t yet know which retail or restaurant breach caused this particular breach.
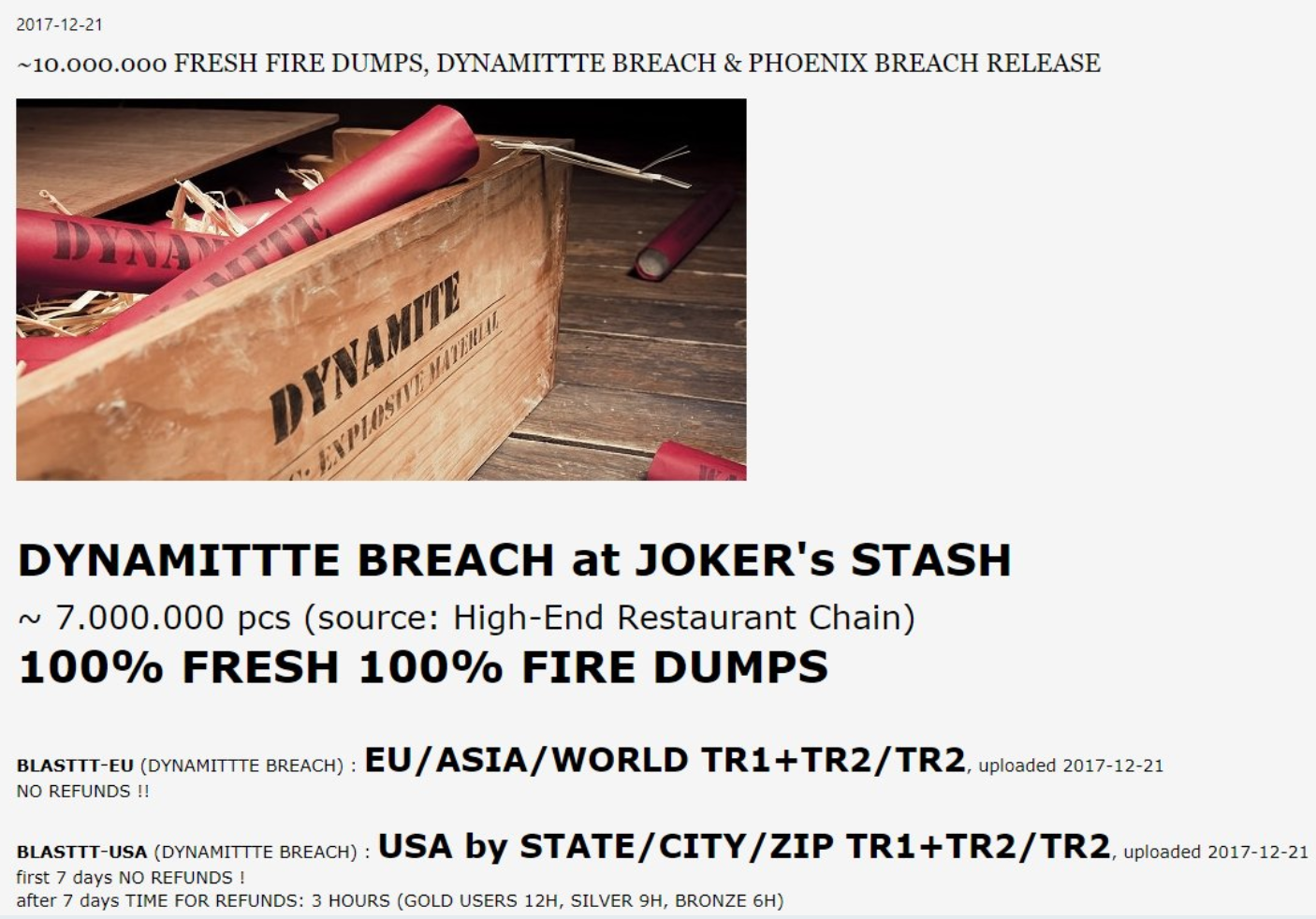
An advertisement for a large new batch of stolen credit card accounts for sale at the Joker’s Stash Dark Web market.
Translation: These stolen cards were far more likely to still be active and useable after fraudsters encode the account numbers onto fake plastic and use the counterfeits to go shopping in big box stores.
I pinged a couple of sources who track when huge new batches of stolen cards hit the market, and both said the test cards they’d purchased from the Joker’s Stash Dynamittte batch mapped back to customers who all had one thing in common: They’d all recently eaten at a Jason’s Deli location.
Jason’s Deli is a fast casual restaurant chain based in Beaumont, Texas, with approximately 266 locations in 28 states. Seeking additional evidence as to the source of the breach, I turned to the Jason’s Deli Web site and scraped the ZIP codes for their various stores across the country. Then I began comparing those ZIPs with the ZIPs tied to this new Dynamittte batch of cards at Joker’s Stash.
Checking my work were the folks at Mindwise.io, a threat intelligence startup in California that monitors Dark Web marketplaces and tries to extract useful information from them. Mindwise found a nearly 100 percent overlap between the ZIP codes on the “Blasttt-US” unit of the Dynamittte cards for sale and the ZIP codes for Jason’s Deli locations.
Reached for comment, Jason’s Deli released the following statement:
“On Friday, Dec. 22, 2017, our company was notified by payment processors – the organizations that manage the electronic connections between Jason’s Deli locations and payment card issuers – that MasterCard security personnel had informed it that a large quantity of payment card information had appeared for sale on the ‘dark web,’ and that an analysis of the data indicated that at least a portion of the data may have come from various Jason’s Deli locations.”
“Jason’s Deli’s management immediately activated our response plan, including engagement of a leading threat response team, involvement of other forensic experts, and cooperation with law enforcement. Among the questions that investigators are working to determine is whether in fact a breach took place, and if so, to determine its scope, the method employed, and whether there is any continuing breach or vulnerability.”
“The investigation is in its early stages and, as is typical in such situations, we expect it will take some time to determine exactly what happened. Jason’s Deli will provide as much information as possible as the inquiry progresses, bearing in mind that security and law enforcement considerations may limit the amount of detail we can provide.”
It’s important to note that the apparent breach at Jason’s Deli almost certainly does not correspond to 7 million cards; typically, carding shop owners will mix cards stolen from multiple breaches into one much larger batch (Dynamittte), and often further subdivide the cards by region (US vs. European cards).
As run-of-the-mill as these card breaches have become, it’s still remarkable even in smaller batches of cards like those apparently stolen from Jason’s Deli customers just how many financial institutions are impacted with each breach.
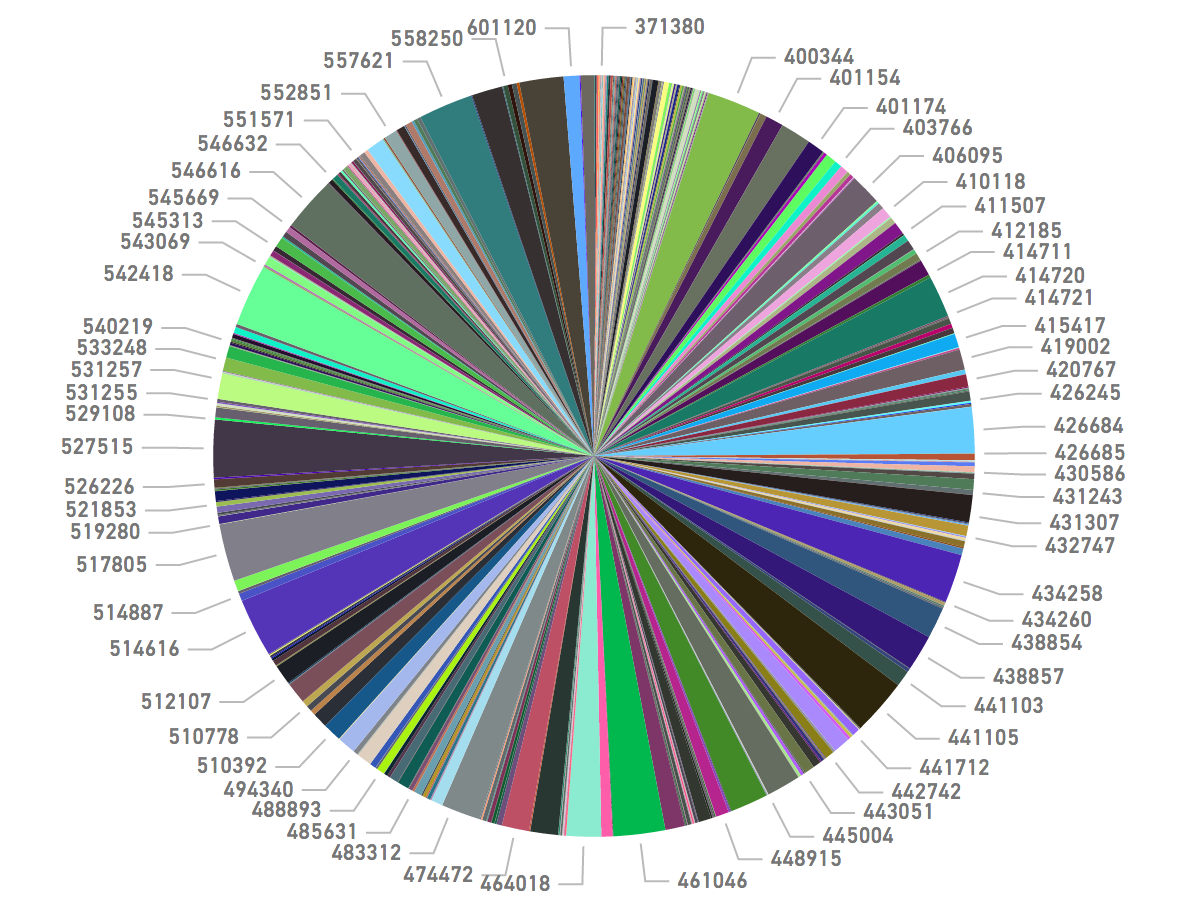
Banks impacted by the apparent breach at Jason’s Deli, sorted by Bank ID Number (BIN) — i.e. the issuer identified by the first six digits in the card number.
Mindwise said it was comfortable concluding that at least 170,000 of the cards for put up for sale this past week on Joker’s Stash map back to Jason’s Deli locations. That may seem like a drop in the bucket compared to the 40 million cards that thieves hauled away from Target four years ago, but the cards stolen from Jason’s Deli customers were issued by more than 250 banks and credit unions, most of which will adopt differing strategies on how to manage fraud on those cards.
In other words, by moving down the food chain to smaller but far more plentiful and probably less secure merchants (either by choice or because the larger stores became a harder target) — and by mixing cards stolen from multiple breaches — the fraudsters have made it less likely that breaches at chain stores will be detected and remediated quickly, thereby prolonging the value and use of the stolen cards put up for sale in underground marketplaces.
All that said, it’s really not worth it to spend time worrying about where your card number may have been breached, since it’s almost always impossible to say for sure and because it’s common for the same card to be breached at multiple establishments during the same time period.
Just remember that although consumers are not liable for fraudulent charges, it may still fall to you the consumer to spot and report any suspicious charges. So keep a close eye on your statements, and consider signing up for text message notifications of new charges if your card issuer offers this service. Most of these services also can be set to alert you if you’re about to miss an upcoming payment, so they can also be handy for avoiding late fees and other costly charges.
Related reading (i.e., other breach stories confirmed with ZIP code analysis):
Breach at Sonic Drive-in May Have Impacted Millions of Credit, Debit Cards
Zip Codes Show Extent of Sally Beauty Breach
Data: Nearly All U.S. Home Depot Stores Hit
Cards Stolen in Target Breach Flood Underground Markets
from
https://krebsonsecurity.com/2017/12/4-years-after-target-the-little-guy-is-the-target/
No comments:
Post a Comment