Not long ago, phishing attacks were fairly easy for the average Internet user to spot: Full of grammatical and spelling errors, and linking to phony bank or email logins at unencrypted (http:// vs. https://) Web pages. Increasingly, however, phishers are upping their game, polishing their copy and hosting scam pages over https:// connections — complete with the green lock icon in the browser address bar to make the fake sites appear more legitimate.
According to stats released this week by anti-phishing firm Phishlabs, nearly 25 percent of all phishing sites in the third quarter of this year were hosted on HTTPS domains — almost double the percentage seen in the previous quarter.
“A year ago, less than three percent of phish were hosted on websites using SSL certificates,” wrote Crane Hassold, the company’s threat intelligence manager. “Two years ago, this figure was less than one percent.”
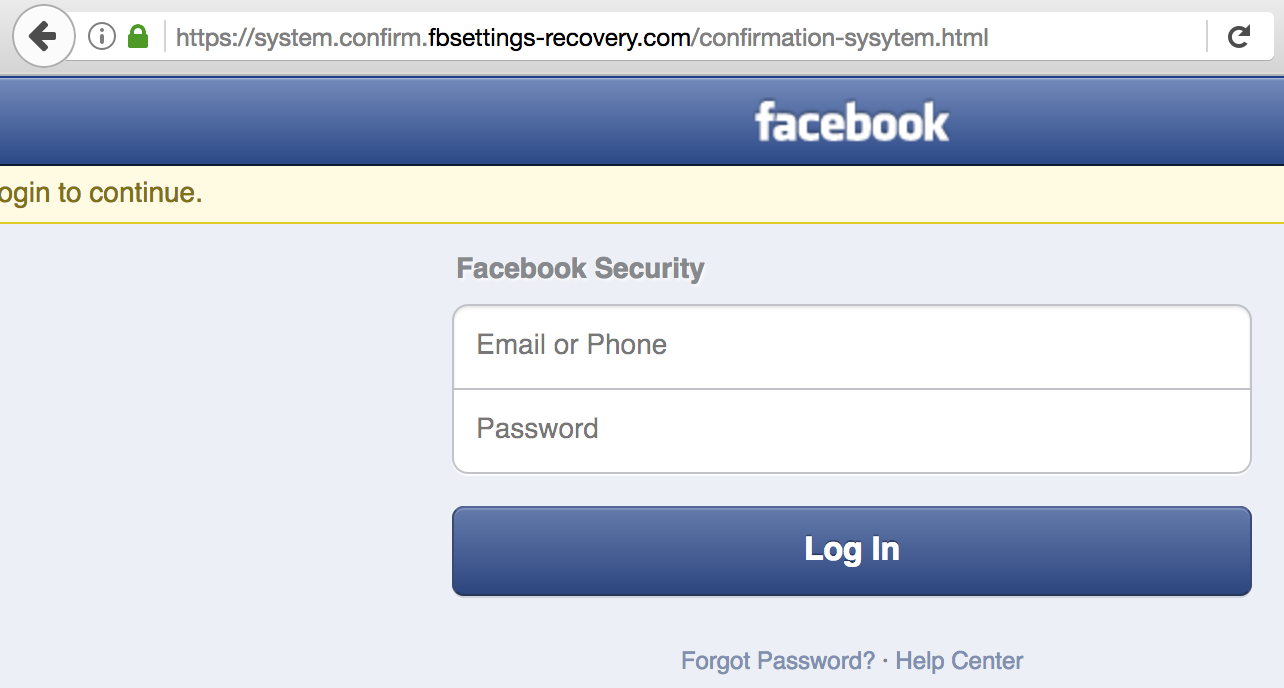
A currently live Facebook phishing page that uses https.
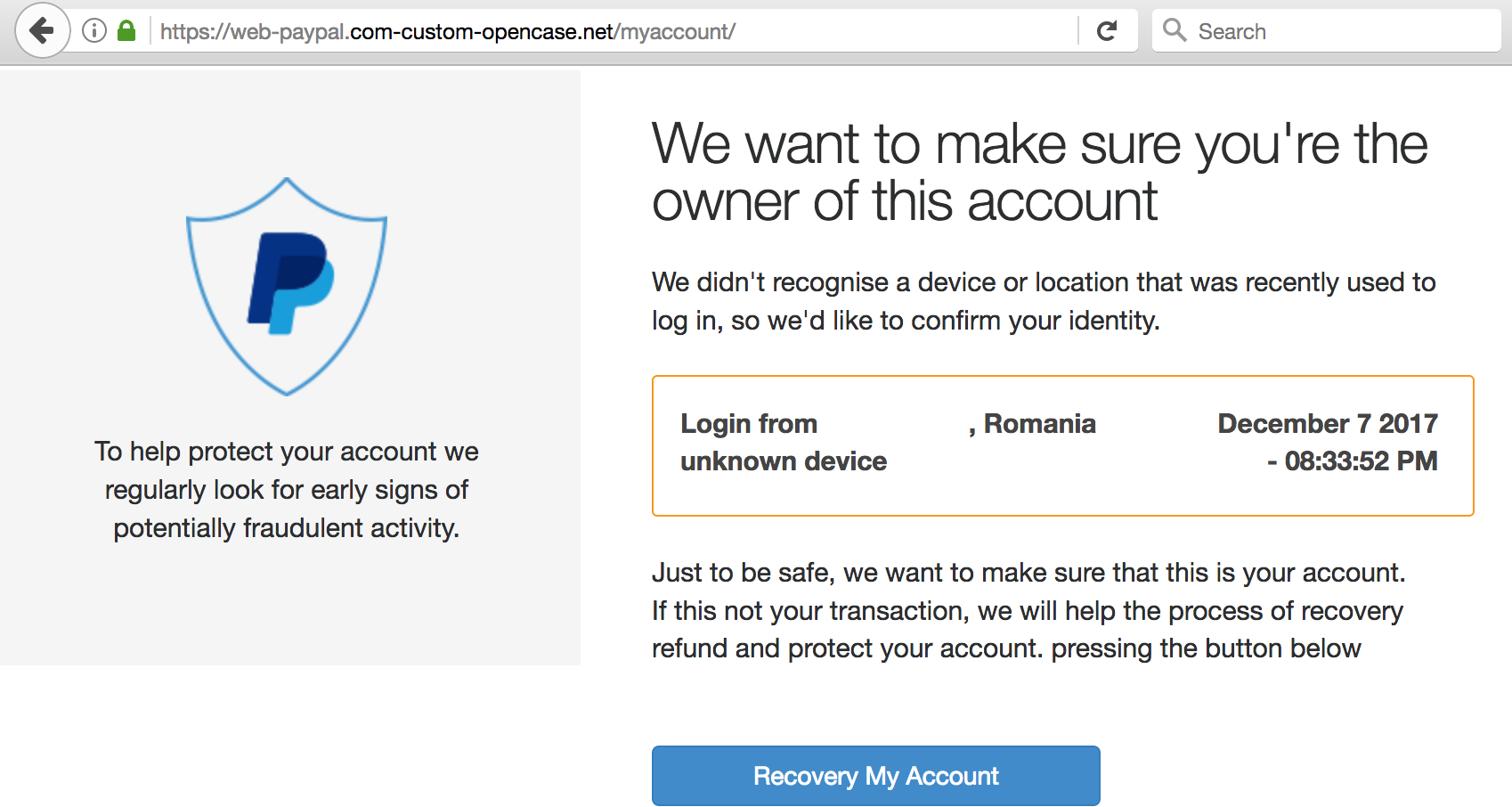
As shown in the examples above (which KrebsOnSecurity found in just a few minutes of searching via phish site reporting service Phishtank.com), the most successful phishing sites tend to include not only their own SSL certificates but also a portion of the phished domain in the fake address.
Why are phishers more aggressively adopting HTTPS Web sites? Traditionally, many phishing pages are hosted on hacked, legitimate Web sites, in which case the attackers can leverage both the site’s good reputation and its SSL certificate.
Yet this, too, is changing, says Phishlabs’ Hassold.
“An analysis of Q3 HTTPS phishing attacks against PayPal and Apple, the two primary targets of these attacks, indicates that nearly three-quarters of HTTPS phishing sites targeting them were hosted on maliciously-registered domains rather than compromised websites, which is substantially higher than the overall global rate,” he wrote. “Based on data from 2016, slightly less than half of all phishing sites were hosted on domains registered by a threat actor.”
Hassold posits that more phishers are moving to HTTPS because it helps increase the likelihood that users will trust that the site is legitimate. After all, your average Internet user has been taught for years to simply “look for the lock icon” in the browser address bar as assurance that a site is safe.
Perhaps this once was useful advice, but if so its reliability has waned over the years. In November, Phishlabs conducted a poll to see how many people actually knew the meaning of the green padlock that is associated with HTTPS websites.
“More than 80% of the respondents believed the green lock indicated that a website was either legitimate and/or safe, neither of which is true,” he wrote.
What the green lock icon indicates is that the communication between your browser and the Web site in question is encrypted; it does little to ensure that you really are communicating with the site you believe you are visiting.
At a higher level, another reason phishers are more broadly adopting HTTPS is because more sites in general are using encryption: According to Let’s Encrypt, 65% of web pages loaded by Firefox in November used HTTPS, compared to 45% at the end of 2016.
Also, phishers no longer need to cough up a nominal fee each time they wish to obtain a new SSL certificate. Indeed, Let’s Encrypt now gives them away for free.
The major Web browser makers all work diligently to index and block known phishing sites, but you can’t count on the browser to save you:
So what can you do to make sure you’re not the next phishing victim?
Don’t take the bait: Most phishing attacks try to convince you that you need to act quickly to avoid some kind of loss, cost or pain, usually by clicking a link and “verifying” your account information, user name, password, etc. at a fake site. Emails that emphasize urgency should be always considered extremely suspect, and under no circumstances should you do anything suggested in the email.
Phishers count on spooking people into acting rashly because they know their scam sites have a finite lifetime; they may be shuttered at any moment. The best approach is to bookmark the sites that store your sensitive information; that way, if you receive an urgent communication that you’re unsure about, you can visit the site in question manually and log in that way. In general, it’s a bad idea to click on links in email.
Links Lie: You’re a sucker if you take links at face value. For example, this might look like a link to Bank of America, but I assure you it is not. To get an idea of where a link goes, hover over it with your mouse and then look in the bottom left corner of the browser window.
Yet, even this information often tells only part of the story, and some links can be trickier to decipher. For instance, many banks like to send links that include ridiculously long URLs which stretch far beyond the browser’s ability to show the entire thing when you hover over the link.
The most important part of a link is the “root” domain. To find that, look for the first slash (/) after the “http://” part, and then work backwards through the link until you reach the second dot; the part immediately to the right is the real domain to which that link will take you.
“From” Fields can be forged: Just because the message says in the “From:” field that it was sent by your bank doesn’t mean that it’s true. This information can be and frequently is forged.
If you want to discover who (or what) sent a message, you’ll need to examine the email’s “headers,” important data included in all email. The headers contain a lot of information that can be overwhelming for the untrained eye, so they are often hidden by your email client or service provider, each of which may have different methods for letting users view or enable headers.
Describing succinctly how to read email headers with an eye toward thwarting spammers would require a separate tutorial, so I will link to a decent one already written at About.com. Just know that taking the time to learn how to read headers is a useful skill that is well worth the effort.
Keep in mind that phishing can take many forms: Why steal one set of login credentials for a single brand when you can steal them all? Increasingly, attackers are opting for approaches that allow them to install a password-snarfing Trojan that steals all of the sensitive data on victim PCs.
So be careful about clicking links, and don’t open attachments in emails you weren’t expecting, even if they appear to come from someone you know. Send a note back to the sender to verify the contents and that they really meant to send it. This step can be a pain, but I’m a stickler for it; I’ve been known to lecture people who send me press releases and other items as unrequested attachments.
If you didn’t go looking for it, don’t install it: Password stealing malware doesn’t only come via email; quite often, it is distributed as a Facebook video that claims you need a special “codec” to view the embedded content. There are tons of variations of this scam. The point to remember is: If it wasn’t your idea to install something from the get-go, don’t do it.
Lay traps: When you’ve mastered the basics above, consider setting traps for phishers, scammers and unscrupulous marketers. Some email providers — most notably Gmail — make this especially easy.
When you sign up at a site that requires an email address, think of a word or phrase that represents that site for you, and then add that with a “+” sign just to the left of the “@” sign in your email address. For example, if I were signing up at example.com, I might give my email address as krebsonsecurity+example@gmail.com. Then, I simply go back to Gmail and create a folder called “Example,” along with a new filter that sends any email addressed to that variation of my address to the Example folder.
That way, if anyone other than the company I gave this custom address to starts spamming or phishing it, that may be a clue that example.com shared my address with others (or that it got hacked!). I should note two caveats here. First, although this functionality is part of the email standard, not all email providers will recognize address variations like these. Also, many commercial Web sites freak out if they see anything other than numerals or letters, and may not permit the inclusion of a “+” sign in the email address field.
from
https://krebsonsecurity.com/2017/12/phishers-are-upping-their-game-so-should-you/
No comments:
Post a Comment